Reading Room Table Display
| Title | Content | Publication Date |
|---|---|---|
| #StopRansomware: Hive Ransomware |
Alert (AA22-321A)
Read full article, or download PDF version of this article, on the CISA site This advisory uses the MITRE ATT&CK® for Enterprise framework, version 12. See MITRE ATT&CK for Enterprise for all referenced tactics and techniques. *Excerpt taken from cisa.gov | November 30, 2022 |
| Hive Ransomware |
Hive is an exceptionally aggressive, financially-motivated ransomware group known to maintain sophisticated capabilities who have historically targeted healthcare organizations frequently. The Health Sector Cybersecurity Coordination Center (HC3) recommends the Healthcare and Public Health (HPH) Sector be aware of their operations and apply appropriate cybersecurity principles and practices found in this document in defending their infrastructure and data against compromise. The Hive ransomware group has been known to be operational since June of 2021 but in that time has been very aggressive in targeting the US health sector. One report covering the third quarter of 2021 – just months after they began operating – ranks them as the fourth most active ransomware operators in the cybercriminal ecosystem. Another report noted the observation of 355 companies in Hive’s first 100 days of operation. | May 17, 2022 |
| NISTIR 8374- Ransomware Risk Management: A Cybersecurity Framework Profile |
The Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. The profile can be used as a guide to managing the risk of ransomware events. That includes helping to gauge an organization’s level of readiness to counter ransomware threats and to deal with the potential consequences of events. Visit NIST to read more or download PDF. Resource: | March 1, 2022 |
| Threat-Informed Cybersecurity Operations for Healthcare Delivery Organizations |
Healthcare Delivery Organizations (HDO) face a complex set of challenges in their information technology and operational environment, with threats that can impact patient care, business operations, medical devices, facilities, protected health information, and public confidence. A critical element for defense is the Cybersecurity Operations Center (CSOC), which acts as a focal point for an HDO’s cyber threat monitoring and response. This paper provides a framework that aligns with the threats that HDOs face, which cyber leadership can use to help assess the state of their operational cyber defenses and inform planning for future defensive capabilities. | November 29, 2021 |
| CISA Ransomware Resource Hub |
Visit CISA’s Ransomware Resource Hub to access all resources. *Excerpt from www.cisa.gov. | July 19, 2021 |
| Detect Cyber Events | All ransomware has something in common: as it interacts with the host it is trying to lock down, without fail it triggers host logs and network logs that can be used to detect the malicious activity. Unless, that is, the appliances and software responsible for generating those logs were never properly configured. What follows is an overview of the research you will need to do and the kinds of resources you will need to put in place to generate and gather meaningful and sufficient cyber event data. IntroductionIn cybersecurity, “detection” is a loaded term. In the context of NIST’s overarching Cybersecurity Framework, detection includes noticing potentially malicious activity, analyzing what has happened in more detail, and reaching final conclusions about what has happened. There is a lot going on there, all in a single stage. You will notice that data collection, which is a prerequisite for detecting anything within the data, is assumed and not specifically spelled out. For the purposes of our discussion, it is useful to consider the following flow, which is based on NIST’s Incident Response framework but is more granular:
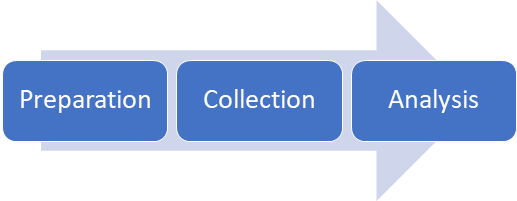
PreparationFor our purposes, preparation is all about knowing your organization and your network:
Preparation is not a one-size-fits-all formula; what is important is to grasp the spirit of preparation and create documentation that makes sense for your organization. It is possible to catch some malicious activity without having done the type of preparation defined here, simply by deploying canned products and analytics. However, skipping this work will reduce your success rate and will also make remediation of an event more confusing, slow, and difficult. Preparation can also include understanding adversary behavior. Knowing this information can help you identify what to look for and where to look for it. This type of preparation is described in greater depth in the Cyber Threat Intelligence resource page. CollectionThis is the collection and aggregation of raw network and host events: an unfiltered view into what is happening on your network. Which process are running, who is logging in, what kinds of packets are being sent from where to where – all of these questions and more should be answered by the data you collect. This data is gathered from sensors, which are utilities, services, or pieces of hardware on your network that sense what is happening and package the information into “events” that you can read and analyze. Typical sensors include: Firewalls Firewalls not only block suspicious traffic, but produce logs of what they’ve seen that can be a rich resource for security analysts. Network Intrusion Detection Systems (NIDS) Commonly known Free Open-source (FOSS) NIDS include Snort, Suricata, and Zeek. While similar to a firewall, they are out-of-band and can be placed anywhere within your network. They are designed to produce alerts that can be a great starting point for investigations. They can also be configured to give you metadata for every flow on your network, malicious or not, which gives you tremendous visibility into what is happening on your network. Windows Event Logs These host logs are incredibly detailed and can be configured to alert you to almost any kind of activity on a particular computer, ranging from a user logging in, to a process spawning, to a registry key being modified. Auditd While not as detailed, Auditd logs serve much the same purpose as Windows Event Logs, on Linux systems. Sysmon This after-market security tool offers alerts for critical host events such as process creation, in a more distilled format than what is offered by Windows Event Logs. Endpoint Detection and Response (EDR) or Host Intrusion Detection System (HIDS) An EDR is essentially a next-generation anti-virus platform that lives on each host in your network and catches malicious activity as it happens. This software typically can be configured to generate detailed logs, which are a valuable source of information to catch hackers as they try to move laterally in your network. Most of these platforms are paid, proprietary software, but they can be well worth it. Windows Defender is an example of an EDR that just happens to be built into the operating system. While do not have to have every log type listed above, the more diversity of logs you have, the more effective your analysis will be. Data from all your sensors typically should be aggregated together in one place, in a normalized schema and time zone, so that you can reference and correlate all the logs conveniently. Most organizations choose to use a Security Information and Event Management (SIEM) platform, which is designed for storing and viewing these logs. Open source examples include Elastic SIEM and Apache Metron. To get all your logs into your SIEM, you will have to configure pipelines, or shippers, that send each log type from its place of origin to your SIEM. The best way to do this varies with each SIEM. AnalysisOnce you have logs consistently flowing into your SIEM, you are ready to analyze them, which is the most important part of Detection! Refer to Health Cyber’s Analytics page for resources and a step-by-step guide for deploying open source analytics on your data. To learn how to gain more insight into your detections, refer to the Cyber Threat Intelligence page. Resources:
| July 15, 2021 |
| Rubric for Applying CVSS to Medical Devices |
The Common Vulnerability Scoring System (CVSS) assists organizations in assessing the severity of vulnerability to determine the urgency and priority of the response. CVSS was developed for enterprise IT systems and does not adequately reflect the clinical environment and potential patient safety issues. To address these challenges, MITRE developed the “Rubric for Applying CVSS to Medical Devices.” The CVSS Rubric consists of a structured set of questions and corresponding decision flow diagrams, along with medical device specific examples and guidance, to help assess a medical device vulnerability in a consistent and standardized way. In October 2020, FDA qualified the CVSS Rubric as a Medical Device Development Tool. URL to the paper on MITRE.ORG https://www.mitre.org/md-cvss-rubric | July 6, 2021 |
| Zero Trust Architecture (ZTA) |
Zero Trust Architecture (ZTA) can reduce the attack surface and limit adversarial lateral movement thereby reducing the impact of ransomware. The implementation of ZTA requires the integration of existing and new capabilities, as well as buy-in across the enterprise. Successful implementations will require multi-year planning that includes determination of drivers and use cases, policy development, architecture development, technology readiness assessment, pilots, user training, and phasing of deployments. The movement towards Zero Trust Architectures (ZTA) aligns with cybersecurity modernization strategies and practices to deter and defend against dynamic threats both inside and outside traditional enterprise perimeters. A key driver for ZTA adoption across the federal government space is the “Executive Order on Improving the Nation’s Cybersecurity” released from President Biden on May 12, 2021, directing executive agencies to “develop a plan to implement Zero Trust Architecture.” The ZTA Tech Watcher report explores the state of the technology today and provides background, applicability, and benefits to organizations, outstanding challenges and issues, and recommendations. The paper can be found at https://www.mitre.org/publications/technical-papers/zero-trust-architectures-are-we-there-yet; | July 6, 2021 |
| CISA Fact Sheet Rising Ransomware Threat to OT Assets |
CISA has published the Rising Ransomware Threat to OT Assets fact sheet in response to the recent increase in ransomware attacks targeting operational technology (OT) assets and control systems. The guidance: · Provides steps to prepare for, mitigate against, and respond to attacks; · Details how the dependencies between an entity’s IT and OT systems can provide a path for attackers; and · Explains how to reduce the risk of severe business degradation if affected by ransomware | June 14, 2021 |
| Principles and Practices for Medical Device Cybersecurity |
Download “Principles and Practices for Medical Device Cybersecurity” PDF.
*Excerpt from http://www.imdrf.org/. | June 4, 2021 |
| FBI Watch – TLP:WHITE Report |
*Excerpt from https://www.aha.org. | May 24, 2021 |
| Ransomware Protection and Response |
To read all information, visit the Computer Security Resource Center on the NIST site.
*Exerpt from https://csrc.nist.gov/. | May 19, 2021 |
| Combating Ransomware: A Comprehensive Framework for Action: Key Recommendations from the Ransomware Task Force |
Visit the Institute for Security & Technology site to download PDF.
*Excerpt from securityandtechnology.org. | April 30, 2021 |
| Locked Out: Tackling Australia’s ransomware threat |
Download “Locked Out: Tackling Australia’s Ransomware Threat” as PDF.
*Excerpt from https://www.homeaffairs.gov.au/. | March 20, 2021 |
| NIST Cybersecurity Framework |
Assess Technical ReadinessThe National Institute of Standards and Technology (NIST) Cybersecurity Framework is voluntary guidance intended to help organizations to better manage and reduce cybersecurity risk. The Framework provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand and communicate to all stakeholders. The NIST Cybersecurity Framework consists of three-parts:
| February 25, 2021 |
| No-Cost Malicious Domain Blocking and Reporting for U.S. Hospitals |
No-Cost Cyber Defense for U.S. Hospitals “The Center for Internet Security® (CIS®), in partnership with Akamai, is offering the Malicious Domain Blocking and Reporting (MDBR) service AT NO COST to all public and private hospitals and related healthcare organizations in the United States. This service provides an additional layer of cybersecurity protection that is proven, effective, and easy to deploy. MDBR is a fully-managed proactive domain security service, with CIS and Akamai fully maintaining the systems required to provide the service. Once an organization points its DNS requests to Akamai’s DNS server IP addresses, every DNS lookup will be compared against a list of known and suspected malicious domains. Attempts to access known malicious domains associated with malware, phishing, ransomware, and other cyber threats will be blocked and logged. The logged data is then provided by Akamai to CIS’s Security Operations Center (SOC). The SOC uses this data to perform detailed analysis and aggregate reporting for the benefit of the hospital community, as well as organization-specific reporting and intelligence services. If circumstances require, remediation assistance is provided for each organization that implements the service.”* Read about No-Cost Cyber Defense for U.S. Hospitals.
*Excerpt from www.cisecurity.org. | February 23, 2021 |
| Protecting Data from Ransomware and Other Data Loss Events |
Read more about A Guide for MSPs to Conduct, Maintain, and Test Backup Files and to download PDF.
*Excerpt from csrc.nist.gov. | February 21, 2021 |
| Design Defenses |
IT and cybersecurity practitioners are responsible for the technical implementation of defensive technologies. Before a ransomware incident occurs, healthcare organizations should have an effective security architecture in place to identify, protect, detect, respond to and recover from ransomware. The NIST Ransomware Practice Guides below provide reference designs using existing commercial products that could aid an organization in remediating gaps in an organization’s cybersecurity implementation. NIST SPECIAL PUBLICATION (SP) 1800-25 This NIST Ransomware Practice Guide shows how organizations can develop and implement appropriate actions/technologies to remediate gaps in an organization-cybersecurity implementation using existing commercial products, which can be deployed before a detected cybersecurity event. NIST SPECIAL PUBLICATION (SP) 1800-11 This NIST Ransomware Practice Guide shows how organizations can develop and implement appropriate actions and use various technologies to recover from a cybersecurity event.
| February 21, 2021 |
| Cybersecurity Maturity Models |
EVALUATE CYBERSECURITY MATURITYHHS recently published an overview of three Cybersecurity Maturity Models including the NIST Cybersecurity Framework. These models allow an organization to baseline their current capabilities against best practices. Download the presentation on Cybersecurity Maturity Models.
| February 19, 2021 |
| Podcast Interview: Cyber and Supply Chain Threats to the Health Care Sector |
Listen to Podcast or read transcript.
*Excerpt from www.dni.gov. | February 18, 2021 |
| Designing Cyber Resilient Systems (NIST SP 800-160 Vol. 2) | NIST Special Publication 800-160 Volume 2, Designing Cyber Resilient Systems: A Systems Security Engineering Approach, defines cyber resiliency as the ability to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks, or compromises on cyber resources. NIST SP 800-160 Vol. 2 offers a framework for understanding the problem space and the cyber resiliency solution space. It supports engineering analysis and judgment, identifying factors to consider when making trade-offs among different possible capabilities. It includes notional worked examples, to illustrate how cyber resiliency concepts and technologies can be tailored to different environments. For healthcare providers, implementing cyber resiliency could mean preventing loss of life. Visit the NIST site to download the publication.
| February 16, 2021 |
| Stop that Phish |
Learn more about phishing on the SANS site.
*Excerpt from www.sans.org. | February 16, 2021 |
| SEI Cyber Minute: Mitigating Ransomware |
Watch Rotem Guttman in this SEI Cyber Minute as he discusses “Mitigating Ransomware.”
| February 11, 2021 |
| Health Care Industry Cybersecurity Task Force |
Read more about the Health Care Industry Cybersecurity Task Force.
*Excerpt from www.phe.gov. | February 11, 2021 |
| HHS 405(d) Aligning Health Care Industry Security Approaches | Provides industry-led consensus-based guidelines, practices, and methodologies that aim to raise awareness, provide vetted cybersecurity practices, and move organizations towards consistency in mitigating the current most pertinent cybersecurity threats to the HPH sector. | February 11, 2021 |
| Cybersecurity Toolkit for Digital Health |
Visit Mass Digital Health site to access all resources.
*Excerpt from massdigitalhealth.org. | February 11, 2021 |
| SANS: Internet Storm Center (ISC) |
Vist the Internet Storm Center.
*Excerpt from isc.sans.edu. | February 11, 2021 |
| FBI: InfraGard Portal |
*Excerpt from infragard.org. | February 11, 2021 |
| US Computer Emergency Response Team (US-CERT) |
As part of its mission, CISA leads the effort to enhance the security, resiliency, and reliability of the Nation’s cybersecurity and communications infrastructure.
| February 11, 2021 |
| Common Vulnerability Scoring System Special Interest Group (SIG) |
*Excerpt from first.gov. | February 10, 2021 |
| Common Vulnerabilities and Exposures (CVE) |
CVE® is a list of records—each containing an identification number, a description, and at least one public reference—for publicly known cybersecurity vulnerabilities.
| February 10, 2021 |
| 11 Strategies of a World-Class Cybersecurity Operations Center |
If you are getting started in cybersecurity operations, evolving your existing security operations center (SOC), or engaging with a SOC regularly, MITRE offers free downloads of 11 Strategies of a World-Class Cybersecurity Operations Center—both for the 20-page summary document and the full textbook. Fully revised, this second edition of the popular 10 Strategies of a World-Class Cybersecurity Operations Center includes new material and evolved thinking to bring a fresh approach to excelling at cybersecurity operations and leveraging up your cyber defenses. You will learn to:
| February 10, 2021 |
| CISA Cyber Resource Hub | Cybersecurity Resources to help agencies make data informed risk decisions, by gaining visibility with vulnerability trends, adversarial activities and, most important, effective mitigations to implement for better protection of their networks. Visit CISA’s Cyber Resource Hub to access all resources.
| February 5, 2021 |
| Cyber Resilience Review (CRR) |
The Department of Homeland Security/Cybersecurity and Infrastructure Security Agency (DHS/CISA) offers a Cyber Resilience Review.
Visit the CISA site to access all resources.
*Excerpt from us-cert.cisa.gov.
| February 5, 2021 |
| Cyber Tabletop Exercises |
Evaluate your cyber response planCyber Tabletop Exercises (TTX) are a way to evaluate your cyber response plan with scenarios that identify gaps between what you’ve planned for and what can actually happen, practice roles and responsibilities, and improve communications throughout organizations. Intelligence Driven Exercises and Solutions (IDEAS) is a TTX methodology – during which participants explore dynamic problem sets or threats in a unique way to challenge assumptions, methods, and strategies and bolster understanding. The resources below provide both an overview and detailed description of the methodology. Resources: Other Resources:
| February 1, 2021 |
| Health Information Sharing and Analysis Center (H-ISAC) |
Visit the H-ISAC site for more information and resources.
*Excerpt from h-isac.org. | February 1, 2021 |
| Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients |
Visit the Public Health Emergency site to access all documentation.
*Excerpt from www.phe.gov. | February 1, 2021 |
| Health Sector Cybersecurity Coordination Center (HC3) Homepage |
Visit HC3 site to access all products.
*Excerpt from www.hhs.gov. | February 1, 2021 |
| Health Sector Coordinating Council |
Read more on the HSCC site or download “HICP: Managing and Protecting Patients” PDF directly.
*Excerpt from healthsectorcouncil.org. | February 1, 2021 |
| Cyber Assessments |
Cyber Assessments include a full range of vulnerability and penetration testing, and adversary assessment methods to bolster an organization’s ability to identify, protect, and detect ransomware threats. By tailoring and applying assessment methodologies and tools focused on business requirements, employing these methods can help improve an organization’s ability to assess and manage their enterprise ransomware risk. Download Cyber Assessment PDF.
| January 28, 2021 |
| User Awareness Training |
TRAIN STAFF TO AVOID INFECTIONUsers are often the most effective cyber sensors. User awareness training helps every employee in your organization to better recognize, avoid, and report potential threats that can compromise critical systems via known attack vectors, including phishing and ransomware. MITRE has implemented a program to train users on how to recognize and handle suspicious emails. We provided an overview of how to establish such a program. The EARNEST Practice helps educate End Users to be effective Cyber Sensors. Resources: | January 25, 2021 |
| Cyber Threat Intelligence | Cyber threat intelligence understands and analyzes real-world threats and adversaries to share data and knowledge utilizing the traditional intelligence cycle to evolve from data, through information, to intelligence. It may be tactical, operational, or strategic in nature, informing activities ranging from remediation to threat hunting and strategic organizational risk management. Understand the AdversaryUnderstanding the adversary is one of the first steps in preparing a threat-informed defense. This paper describes how incremental developments in ransomware since 1989 have led to the emergence of a ransomware business model. This business models allows the highly damaging ransomware infections seen today. To learn more about this evolution and common initial access vectors used by ransomware groups, read the Evolution of Ransomware paper. Defending Against Ransomware: A Cyber Threat Intelligence PrimerA Cyber threat intelligence capability can help organizations take a threat-informed defense approach to protecting itself from a wide range of malicious cyber activity, including ransomware. A robust CTI program will generally follow the “intelligence cycle” – Planning and Direction, Collection, Processing, Analysis and Production, and Dissemination and Feedback – to ensure it is meeting the expectations of stakeholders and maturing to meet evolving demands. This guide is intended to assist organizations interested in establishing a CTI program and those maturing an existing capability. Read more about Defending Against Ransomware in the PDF. Monitoring Threat IntelligenceThe goal of cyber threat intelligence (CTI) is usually to help an organization focus on understanding their greatest threats by providing analyzed intelligence to assist network defenders and decision-makers in making more informed, threat-based decisions. CTI should be actionable and applicable to both near- and long-term information needs for network defenders and decision-makers. CTI should enable activities and actions at the tactical, operational, and strategic levels, ranging from activities such as specific rules network defenders implement within their environments, to enabling proactive adversary hunting methodologies, and progressing to informing strategic decision-making about limited budgetary and personnel resource allocations. A variety of unclassified, commercial, and open-source threat intelligence public and private resources provide insight for organizations to the latest threats. Other Resources:
Cyber Threat Intelligence SharingJOIN COMMUNITY GROUPSWhen possible and appropriate for their circumstances, organizations should share cyber threat intelligence with peer institutions and government entities. Official forums exist to facilitate this, such as HS-ISAC. These sharing relationships can also be an excellent source of threat intelligence for your organization. Other Resources:
| January 25, 2021 |
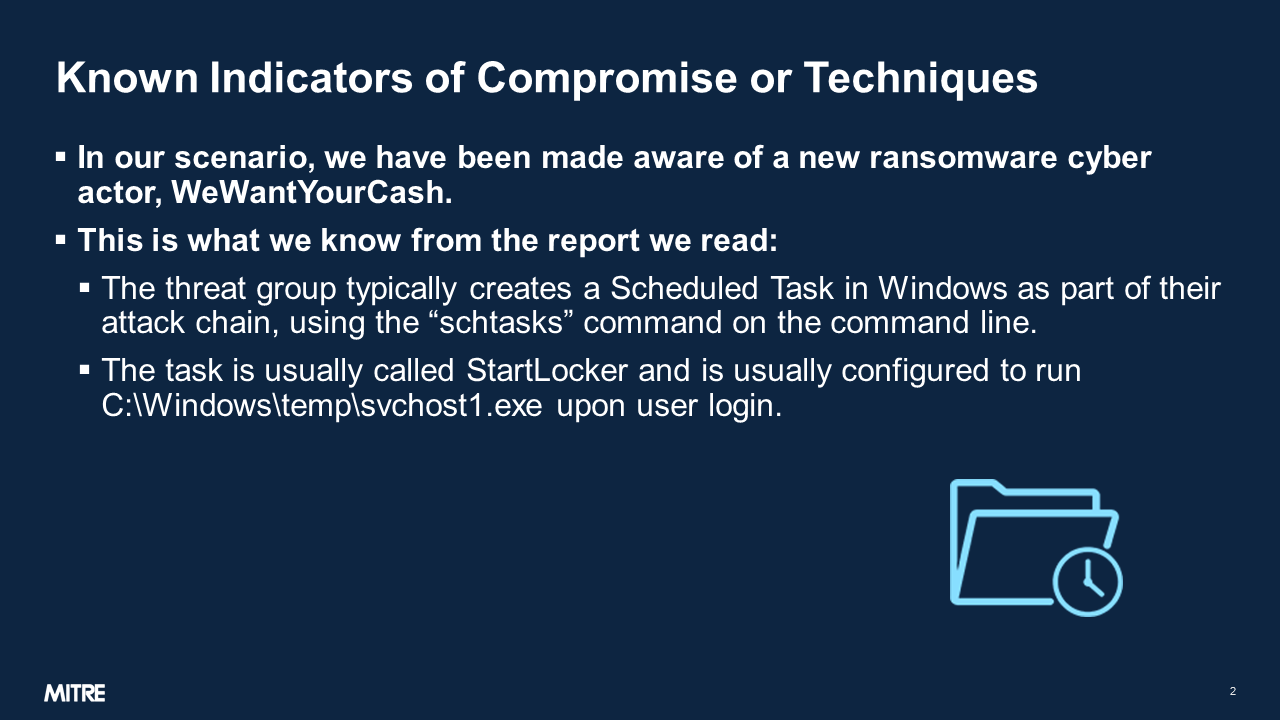
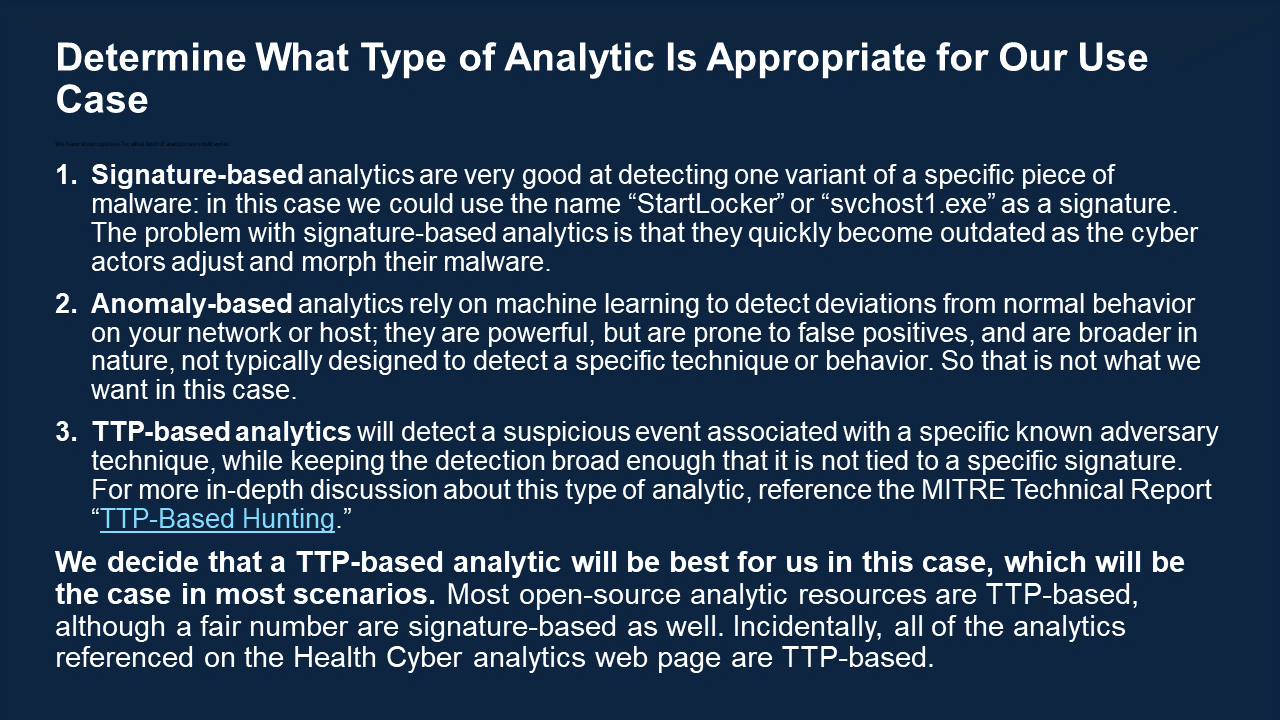
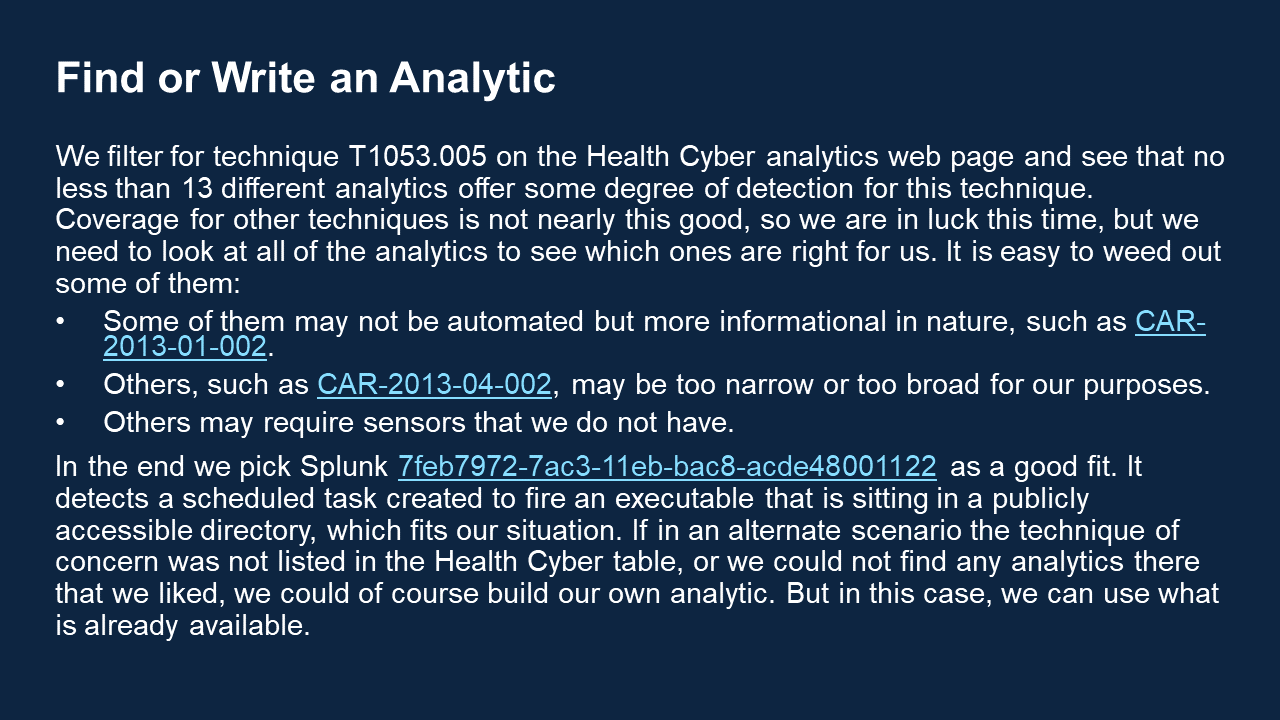
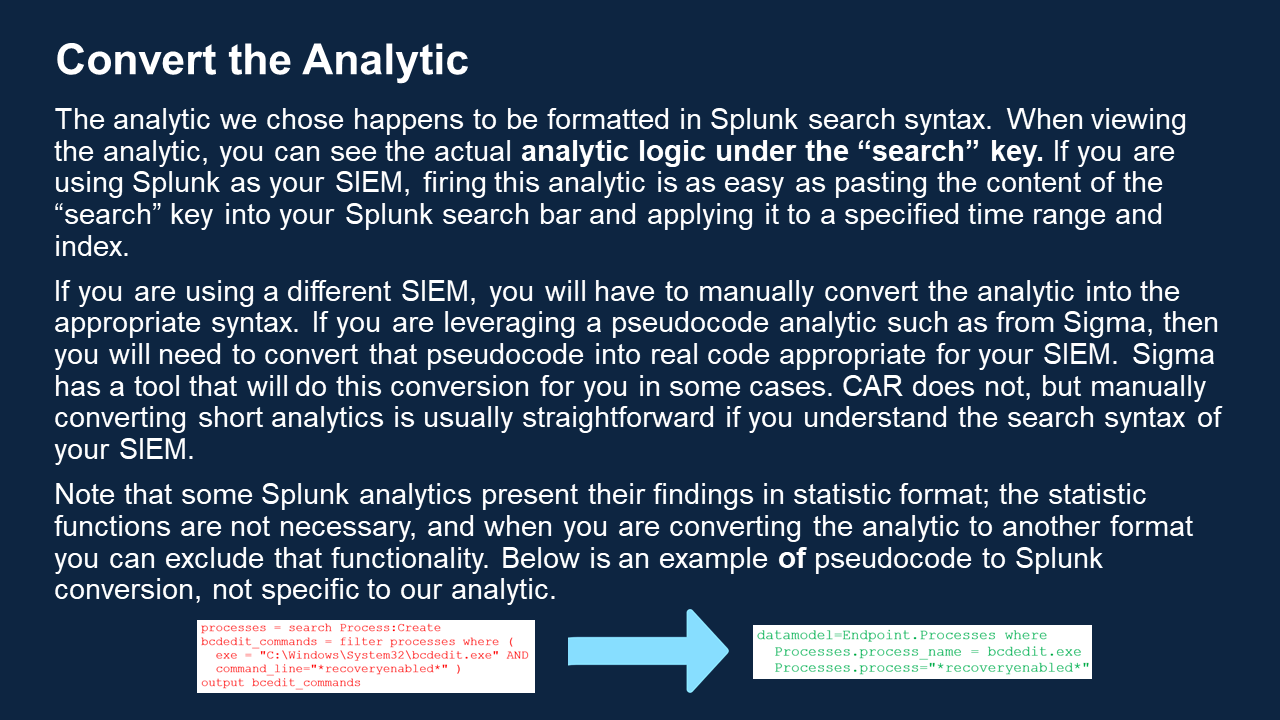
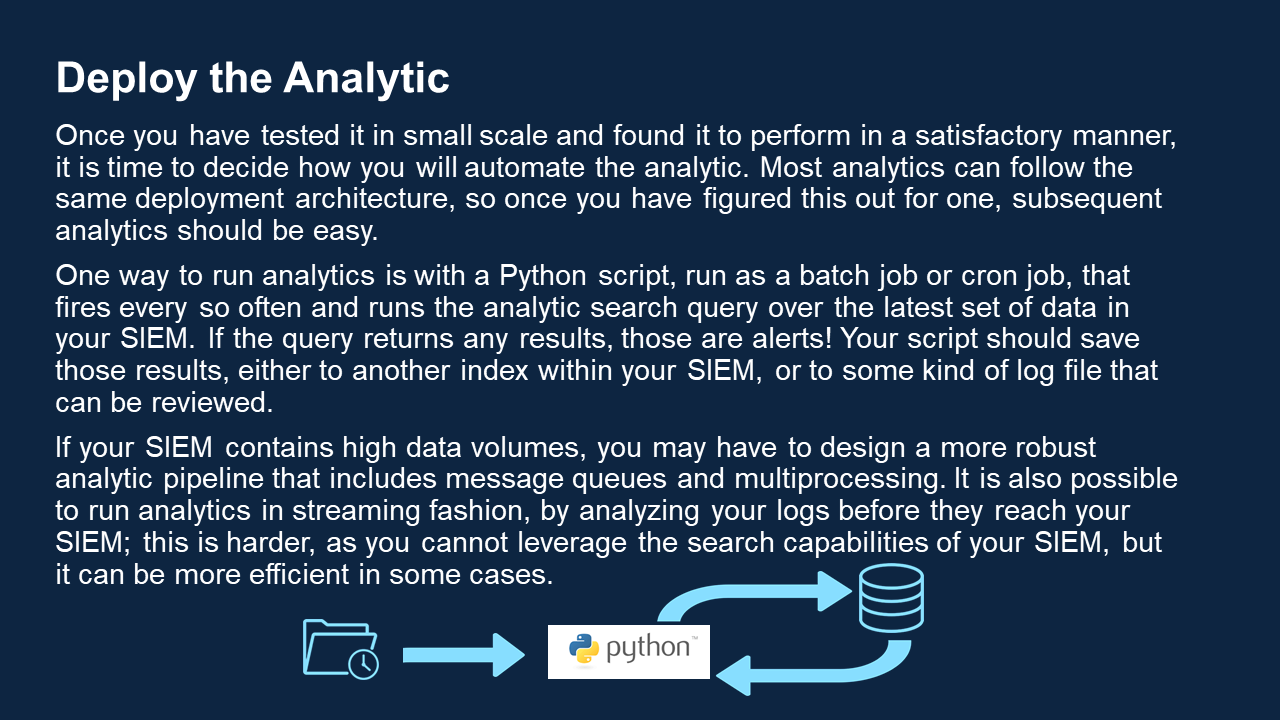
| Deploy Cyber Analytics | Analytics are bits of code that we can use to match up known ransomware tactics and techniques with actual events on our system, as a way of flagging malicious activity. The Analytics Deployment Guide walks through the process of choosing the right analytics for your use case and using them to detect malicious activity in your raw data. Use the table of analytics below as a resource in this process. Read the Analytics Deployment GuideIntroduction and PrerequisitesThis short guide is designed as a quick starter for those who are unfamiliar with the common strategies behind analyzing cyber event data and finding threats. This guide assumes you have done the preparatory work described in the Detection guide. This means that your team is trained, you know which things in your network are most sensitive, you have created the appropriate whitelists, and you have a number of sensors feeding into a SIEM. Review Threat IntelligenceBefore deploying analytics, it is helpful to gain insight into the current threat landscape. We have a heat map of techniques that have recently been used by ransomware threat groups. We have also created a view within the ATT&CK Navigator that highlights the tactics used by ransomware software documented in ATT&CK. Organizations can learn more about tracking ransomware techniques on an ongoing basis on the Cyber Threat Intelligence resources page. Analyze and DetectOnce you have logs consistently flowing into your SIEM and you know what you need to detect, you are ready to do analysis! Analysis comes in three main flavors: Alert-based Investigation Ideally at least one of your sensors will be a security alert-producing product, such as an EDR or NIDS. These sensors have already done some analysis on the raw event data, and have decided to tell you “I think something bad might be happening here,” as opposed to other sensors that are just giving you raw, unanalyzed data. If you have security alert logs, you want to start there. In an alert-based investigation, a human analyst would view the content of the alert and decide whether she agrees that the behavior is suspicious, given her understanding of normal network activity. If she decides it warrants further investigation, she will correlate the alert with the other logs available to her in the SIEM, helping to paint a fuller picture of what is happening. This is why it is important to have as many sensors as possible, to give as much context as possible during an investigation. Hunting Hunting consists of perusing your logs, searching for any suspicious activity, not aided by any automated alerting. This is typically done by skilled, experienced analysts who have been trained to know what to look for and also have expert insight into what normal activity on your network looks like, a result of the Preparation phase. Some organizations choose to bring in a specialized team from time to time to do this type of hunting. Hunting is important, but to some extent it can be like finding a needle in a haystack, without knowing what the needle looks like. This should not be your primary mode of operation. Secondary Automated Analysis While your EDR, firewall, and IDS can produce some security alerts, in many cases they are only guessing at what is bad and will produce false positives, and they will miss other significant events altogether, because they each see only part of the picture. Each security product is blind to the context of what is happening elsewhere on the network. When you have all the data in your SIEM, you have the opportunity to conduct more analysis based on more cohesive knowledge. With this in mind, there are many machine analytics that will parse through the data in your SIEM and produce alerts as appropriate. It is entirely appropriate to write your own analytics, but it also makes sense to take advantage of all the open source analytics that others have already written that may apply to your network as well. Some open source analytic repositories include: Reference Health Cyber’s analytics table for a list of open source analytics you can use to provide maximum detection of the ransomware-related hacking techniques listed in ATT&CK. You will see that numerous analytics are available, and it might not be feasible to deploy them all at once. We recommend starting with those that cover critical techniques that are being leveraged to a high degree by current ransomware threat groups. For a picture of which techniques are trending, reference our Ransomware Heat Map. When you have built or collected the analytics you want, you will need to do several things to run them on your data:
Walk through our analytic deployment scenario for an example of how this all works! | January 25, 2021 |
| Cyber Resiliency | Cyber Resiliency enables organizations to continue to function while under a cyber attack. No matter how strong an organization’s defenses, determined adversaries may penetrate. Implementing resiliency techniques will allow continuation of critical operations and business processes during a successful attack. For healthcare providers, implementing cyber resiliency could mean preventing loss of life. The resources listed below provide additional details on Cyber Resiliency and its implementation. Resources:
| January 25, 2021 |
| Data Integrity: Recovering from Ransomware and Other Destructive Events |
NIST Special Publication (SP) 1800-11 – Data Integrity: Recovering From Ransomware and Other Destructive Events This NIST Ransomware Practice Guide shows how organizations can develop and implement appropriate actions and use various technologies to recover from a cybersecurity event. Visit NIST to read more or to download PDF. The resources below provide additional resources that could aid an organization in recovering from ransomware or other destructive events. Other Resources:
| January 25, 2021 |
| Data Integrity: Detecting and Responding to Ransomware and Other Destructive Events | NIST Special Publication (SP) 1800-26 – Data Integrity: Detecting and Responding to Ransomware and Other Destructive Events This NIST Ransomware Practice Guide shows how organizations can develop and implement appropriate actions and use of technologies to detect and or respond to a detected cybersecurity event. (This practice guide spans both the Detect and Respond CSF domains.) Visit NIST to read more or download PDF. The resources below provide additional resources that could assist an organization in detecting and responding against ransomware or other destructive events. Other Resources:
| January 25, 2021 |
| Data Integrity: Identifying and Protecting Assets Against Ransomware and Other Destructive Events | NIST Special Publication (SP) 1800-25 – Data Integrity: Identifying and Protecting Assets Against Ransomware and Other Destructive Events This NIST Ransomware Practice Guide shows how organizations can develop and implement appropriate actions/technologies to remediate gaps in an organization cybersecurity implementation using existing commercial products, which can be deployed before a detected cybersecurity event. (This practice guide spans both the Identify and Protect CSF domains.) Visit NIST to read more or download PDF. The resources below provide additional resources that could aid an organization in identifying and protecting critical assets against ransomware or other destructive events. Other Resources:
| January 25, 2021 |
| Cyber Operations Rapid Assessment (CORA) |
Assess Cybersecurity OperationsCyber Operations Rapid Assessment (CORA) is a lightweight assessment tool used to evaluate your overall cybersecurity operations and infrastructure. CORA can enable healthcare organizations to gather a snapshot of their cybersecurity operations capabilities and provides specific recommendations for improvement. CORA emphasizes threat analysis, incident prevention and response, and threat intelligence information sharing. CORA is an effective model for an organization seeking a quick review of its cybersecurity operations capability, and as a possible prelude to a more rigorous assessment such as Crown Jewels Analysis (CJA). The resources below provide addition detail on CORA and its application. Resources:
| January 25, 2021 |
| Rubric for Applying CVSS to Medical Devices | The Common Vulnerability Scoring System (CVSS) is an open standard designed to convey vulnerability severity and help determine the urgency and priority of response. When vulnerabilities are discovered in medical devices, medical device manufacturers, typically working with the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC), use CVSS to provide a consistent and standardized way to communicate the severity of a vulnerability between multiple parties, including the medical device manufacturer, hospitals, clinicians, patients, NCCIC, and vulnerability researchers. Read more about the CVSS on MTRE site.
| January 22, 2021 |
| The MITRE Systems Engineering Guide |
Technical Paper The primary purpose of the MITRE Systems Engineering Guide, or SEG, is to convey The MITRE Corporation’s accumulated wisdom on a wide range of systems engineering subjects—sufficient for understanding the essentials of the discipline and for translating this wisdom into practice in your own work environment. Read more about the SEG or request a PDF.
| January 22, 2021 |
| Incident Preparedness and Response |
Medical Device Cybersecurity Regional Incident Preparedness and Response PlaybookTechnical Paper This playbook outlines a framework for health delivery organizations (HDOs) and other stakeholders to plan for and respond to cybersecurity incidents around medical devices, ensure effectiveness of devices, and protect patient safety. This document can help HDOs to prepare for and respond to ransomware attacks. Read more about the Playbook or Download PDF directly. Essential Clean-Slate Cyber Recovery Assessment for Time-Critical ProcessingTechnical Paper This document outlines a framework and set of criteria for assessing an organization’s ability and time to recover from a devastating cyberattack. Assessment criteria provide stakeholders with a common language for analyzing recoverability, and the framework offers a method for performing introspective assessments. These tools can help organizations better ensure that they are prepared and able to execute recovery plans in the event of a ransomware or other cyberattack. Read more about the framework in the PDF.
Resource: The ASPR TRACIE Healthcare System Cybersecurity: Readiness & Response Considerations resource can help healthcare facilities, particularly hospitals, and the systems they may be a part of, understand the roles and responsibilities of stakeholders before, during, and after a cyber incident. Information within this document is specifically related to the effects of a cyber incident on the healthcare operational environment, specifically the ability to effectively care for patients and maintain business practices and readiness during such an event. While the focus of this document is on disruptions associated with a large-scale cyberattack, many strategies and principles outlined are relevant to a range of cybersecurity incidents and healthcare facilities.
| January 22, 2021 |
| Caldera | CALDERA™ is a cybersecurity framework designed to easily run autonomous breach-and-simulation exercises. It can also be used to run manual red-team engagements or automated incident response. It is built on the MITRE ATT&CK™ framework and is an active research project at MITRE. The framework consists of two components:
Visit the CALDERA site to access the tool and documentation.
| January 22, 2021 |
| Ransomware and Breach |
File Agenda:
Download PDF from Health & Human Services Office for Civil Rights.
| January 22, 2021 |
| Ransomware and HIPAA Fact Sheet |
Download “Ransomware and HIPAA Fact Sheet” from the Health & Human Services site.
*Excerpt from www.hhs.gov. | January 22, 2021 |
| Cyber Attack Checklist |
Download Cyber Attack Checklist from Health & Human Services (HHS) site.
*Excerpt from www.hhs.gov. | January 22, 2021 |
| Cyber Security Guidance Material |
Health Information Privacy
Visit the Health & Human Services site for resources.
*Excerpt from www.hhs.gov. | January 22, 2021 |
| Laws and Regulations Enforced by OCR |
Visit the Health & Human Services (HHS) site for all resources.
*Excerpt from www.hhs.gov. | January 22, 2021 |
| Webinar: Combating Ransomware |
Recorded webinar, 1.5hrs long, deep tech
| January 21, 2021 |
| MS-ISAC Ransomware Guide |
This Ransomware Guide includes two resources:
*Excerpt from www.cisa.gov | January 21, 2021 |
| Ransomware Guidance and Resources |
Visit CISA to access all guides and resources.
*Excerpt from www.cisa.gov | January 21, 2021 |
| Ransomware What It Is and What To Do About It |
Read CISA document that covers:
| January 21, 2021 |
| INSIGHTS Ransomware Outbreak |
*Excerpt from us-cert.cisa.gov. | January 21, 2021 |
| CISA, MS-ISAC, NGA & NASCIO Recommend Immediate Action To Safeguard Against Ransomware Attacks |
*Excerpt from us-cert.cisa.gov. | January 21, 2021 |
| Crown Jewels Analysis (CJA) | IDENTIFY CRITICAL ASSETSCrown Jewels Analysis (CJA) is a process for identifying those cyber assets that are most critical to achieve an organization’s key objectives and purpose. CJA can enable healthcare organizations to prioritize and apply limited resources effectively for cyber resiliency, the ability to continue critical operations during a major cyber attack such as ransomware. The resources below provide addition detail on CJA and its application. Resources:
| January 19, 2021 |
| Ransomware Techniques in ATT&CK | UNDERSTAND ADVERSARY TACTICS & TECHNIQUESMITRE ATT&CK® is a globally-accessible, structured knowledge base of adversary cyber tactics, techniques, and sub-techniques that is based on real-world observations. Tactics represent the “why” of an ATT&CK technique or sub-technique. Techniques represent “how” an adversary achieves a tactical objective by performing an action. Sub-techniques further break down behaviors described by techniques into more specific descriptions of how behavior is used to achieve an objective. By using this structured knowledge of how real-world adversaries operate in cyber space to attack their victims, defenders can better prepare for, detect, and protect against those wishing to do them harm. The ATT&CK Navigator is designed to provide basic navigation and annotation of ATT&CK matrices, something that people are already doing today in tools like Excel. For this Ransomware Resource Center, we have created a specific view within the ATT&CK Navigator that highlights the known ransomware actors, software, and their tactics and techniques that are presently documented in ATT&CK. ATT&CK primarily focuses on APT groups though it may also include other advanced groups such as financially motivated actors. Many of the ransomware actors are small-scale cyber criminals, this list is not comprehensive. However, most of the tactics and techniques that are presented here are likely representative of behaviors exhibited by other groups and actors that are not presently cataloged in ATT&CK. MITRE also publishes Deploying Cyber Analytics, which can provide a means to detect known adversary behavior. For this Ransomware Resource Center, we have identified the relevant analytics that pertain to the techniques and subtechniques highlighted in the Navigator view, below. Below are the techniques, software, and groups that are presently documented in ATT&CK. This information continues to evolve. Feedback on relevant information from the user community is welcome at HealthCyber@mitre.org. Common Ransomware Techniques in ATT&CKT1566: Phishing
T1486: Data Encrypted for Impact
T1083: File and Directory Discovery
T1041: Exfiltration over C2
T1490: Inhibit System Recovery
T1562.001: Impair Defenses – Disable or Modify Tools
T1485: Data Destruction
T1489: Service Stop
Ransomware Software in ATT&CK
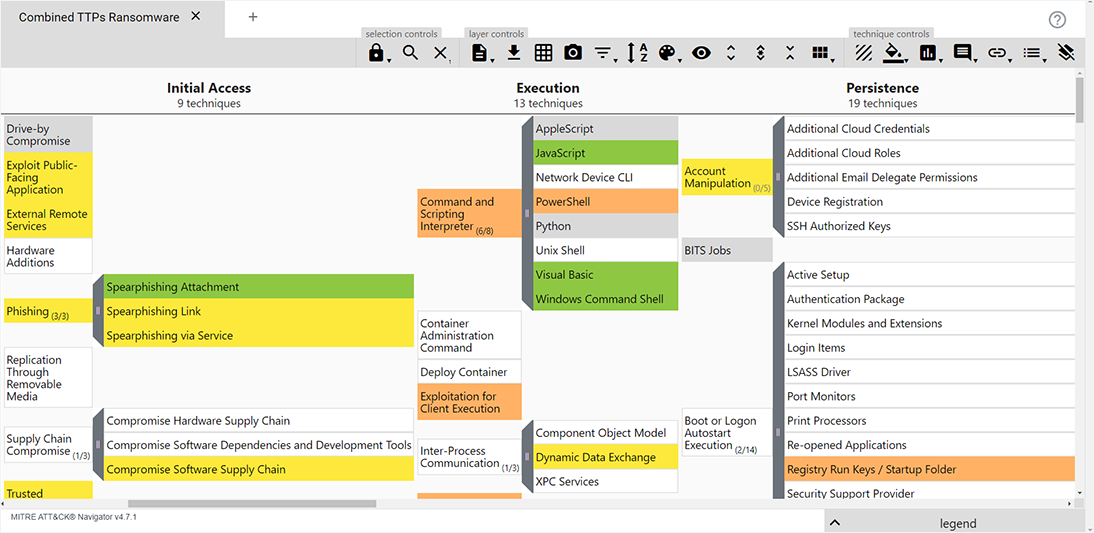
Groups in ATT&CK That Use RansomwareThe ATT&CK Navigator image, below, highlights the techniques in ATT&CK associated with ransomware software, groups that use ransomware, or both according to the legend. Click the image to open ATT&CK Navigator in a new browser window. For a tutorial on how to use the navigator, click on the ? in the upper right corner. To see details, right click on the technique for a menu of options, and select “view technique” or “view tactic”. LEGEND:
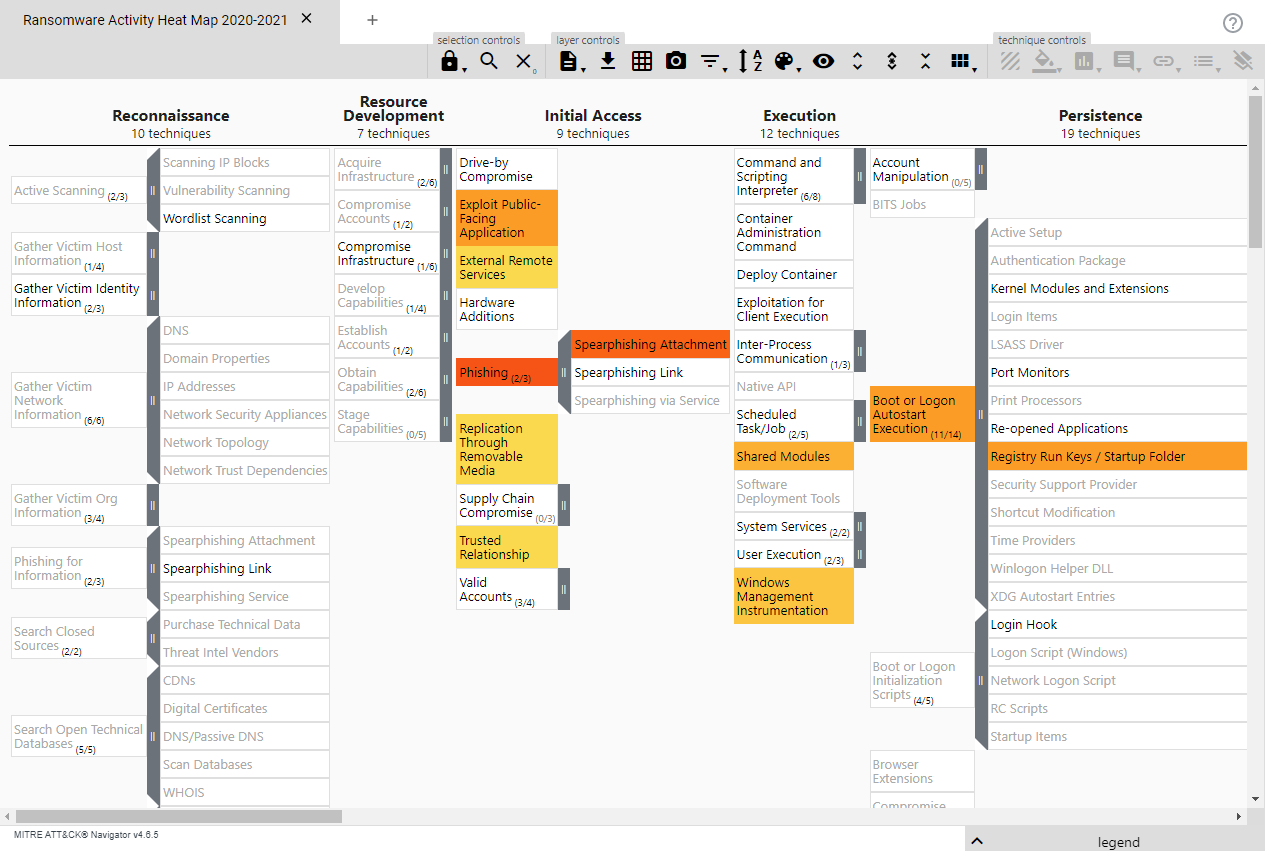
Ransomware Activity Heat MapThe following ATT&CK Navigator image presents techniques that have been leveraged by ransomware threat groups in roughly the last year and a half, based on open-source reporting not limited to ATT&CK. Darker shades represent techniques that have been observed more frequently. Techniques leveraged in the last few months, or those that are present only in third-party software, may not be reflected here. Click image to open Ransomware Activity Heatmap in a new browser window. LEGEND: 
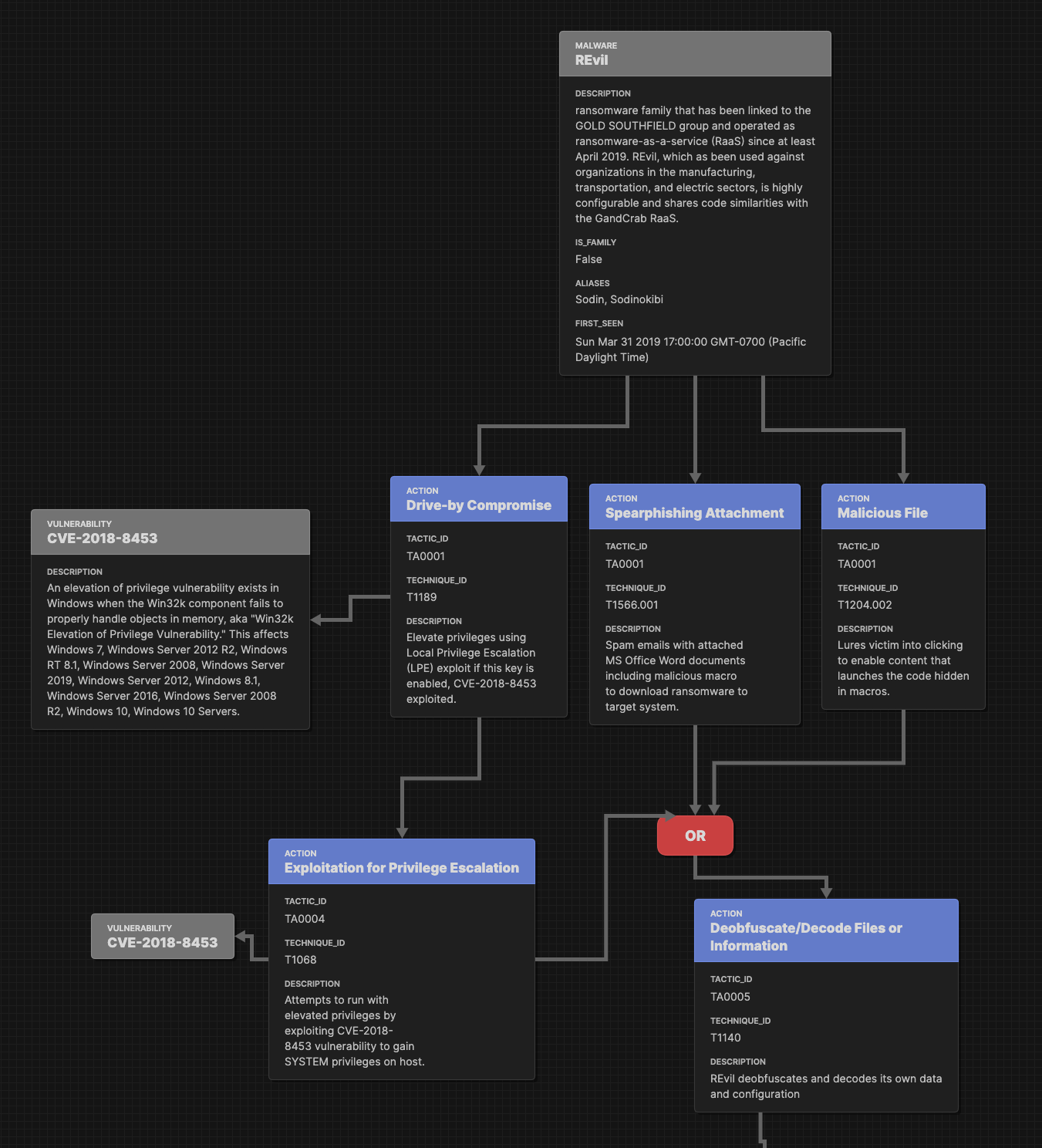
ATTACK FLOWAttack Flow is a language for describing how cyber adversaries combine and sequence various offensive techniques to achieve their goals. Attack Flows help defenders and leaders understand how adversaries operate and improve their own defensive posture. This project is created and maintained by the MITRE Engenuity Center for Threat-Informed Defense in futherance of our mission to advance the state of the art and the state of the practice in threat-informed defense globally. An example of an Attack Flow is seen below in REvil Attack. | January 16, 2021 |
| How to Protect Your Networks from Ransomware |
Download PDF from www.fbi.gov
*Excerpt taken from www.fbi.gov. | January 16, 2021 |
| Protecting Against Ransomware |
Security Tip (ST19-001).
Visit CISA site for more info on Security Tip (ST19-001).
*Excerpt take from us-cert.cisa.gov | January 15, 2021 |
| Ransomware Activity Targeting the Healthcare and Public Health Sector |
Alert (AA20-302A)
Read full article, or download PDF version of this article, on the CISA site. This advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) version 7 framework. See the ATT&CK for Enterprise version 7 for all referenced threat actor tactics and techniques.
*Excerpt taken from us-cert.cisa.gov | January 15, 2021 |
| How to Address the Threat of Ransomware Attacks |
*Video located on dhsconnect.connectsolutions.com. Source found at www.cisa.gov. | January 15, 2021 |
| Security Primer – Ransomware |
Read more information and download PDF on the CIS site.
*Excerpt from www.cisecurity.org. | January 15, 2021 |
| Ransomware: Facts, Threats, and Countermeasures |
Learn more facts, threats, and countermeasures on the CIS site.
*Excerpt from www.cisecurity.org | January 15, 2021 |