Analytics are bits of code that we can use to match up known ransomware tactics and techniques with actual events on our system, as a way of flagging malicious activity. The Analytics Deployment Guide walks through the process of choosing the right analytics for your use case and using them to detect malicious activity in your raw data. Use the table of analytics below as a resource in this process.
Read the Analytics Deployment Guide
Introduction and Prerequisites
This short guide is designed as a quick starter for those who are unfamiliar with the common strategies behind analyzing cyber event data and finding threats. This guide assumes you have done the preparatory work described in the Detection guide. This means that your team is trained, you know which things in your network are most sensitive, you have created the appropriate whitelists, and you have a number of sensors feeding into a SIEM.
Review Threat Intelligence
Before deploying analytics, it is helpful to gain insight into the current threat landscape. We have a heat map of techniques that have recently been used by ransomware threat groups. We have also created a view within the ATT&CK Navigator that highlights the tactics used by ransomware software documented in ATT&CK. Organizations can learn more about tracking ransomware techniques on an ongoing basis on the Cyber Threat Intelligence resources page.
Analyze and Detect
Once you have logs consistently flowing into your SIEM and you know what you need to detect, you are ready to do analysis! Analysis comes in three main flavors:
Alert-based Investigation
Ideally at least one of your sensors will be a security alert-producing product, such as an EDR or NIDS. These sensors have already done some analysis on the raw event data, and have decided to tell you “I think something bad might be happening here,” as opposed to other sensors that are just giving you raw, unanalyzed data. If you have security alert logs, you want to start there. In an alert-based investigation, a human analyst would view the content of the alert and decide whether she agrees that the behavior is suspicious, given her understanding of normal network activity. If she decides it warrants further investigation, she will correlate the alert with the other logs available to her in the SIEM, helping to paint a fuller picture of what is happening. This is why it is important to have as many sensors as possible, to give as much context as possible during an investigation.
Hunting
Hunting consists of perusing your logs, searching for any suspicious activity, not aided by any automated alerting. This is typically done by skilled, experienced analysts who have been trained to know what to look for and also have expert insight into what normal activity on your network looks like, a result of the Preparation phase. Some organizations choose to bring in a specialized team from time to time to do this type of hunting. Hunting is important, but to some extent it can be like finding a needle in a haystack, without knowing what the needle looks like. This should not be your primary mode of operation.
Secondary Automated Analysis
While your EDR, firewall, and IDS can produce some security alerts, in many cases they are only guessing at what is bad and will produce false positives, and they will miss other significant events altogether, because they each see only part of the picture. Each security product is blind to the context of what is happening elsewhere on the network. When you have all the data in your SIEM, you have the opportunity to conduct more analysis based on more cohesive knowledge. With this in mind, there are many machine analytics that will parse through the data in your SIEM and produce alerts as appropriate. It is entirely appropriate to write your own analytics, but it also makes sense to take advantage of all the open source analytics that others have already written that may apply to your network as well. Some open source analytic repositories include:
Reference Health Cyber’s analytics table for a list of open source analytics you can use to provide maximum detection of the ransomware-related hacking techniques listed in ATT&CK. You will see that numerous analytics are available, and it might not be feasible to deploy them all at once. We recommend starting with those that cover critical techniques that are being leveraged to a high degree by current ransomware threat groups. For a picture of which techniques are trending, reference our Ransomware Heat Map.
When you have built or collected the analytics you want, you will need to do several things to run them on your data:
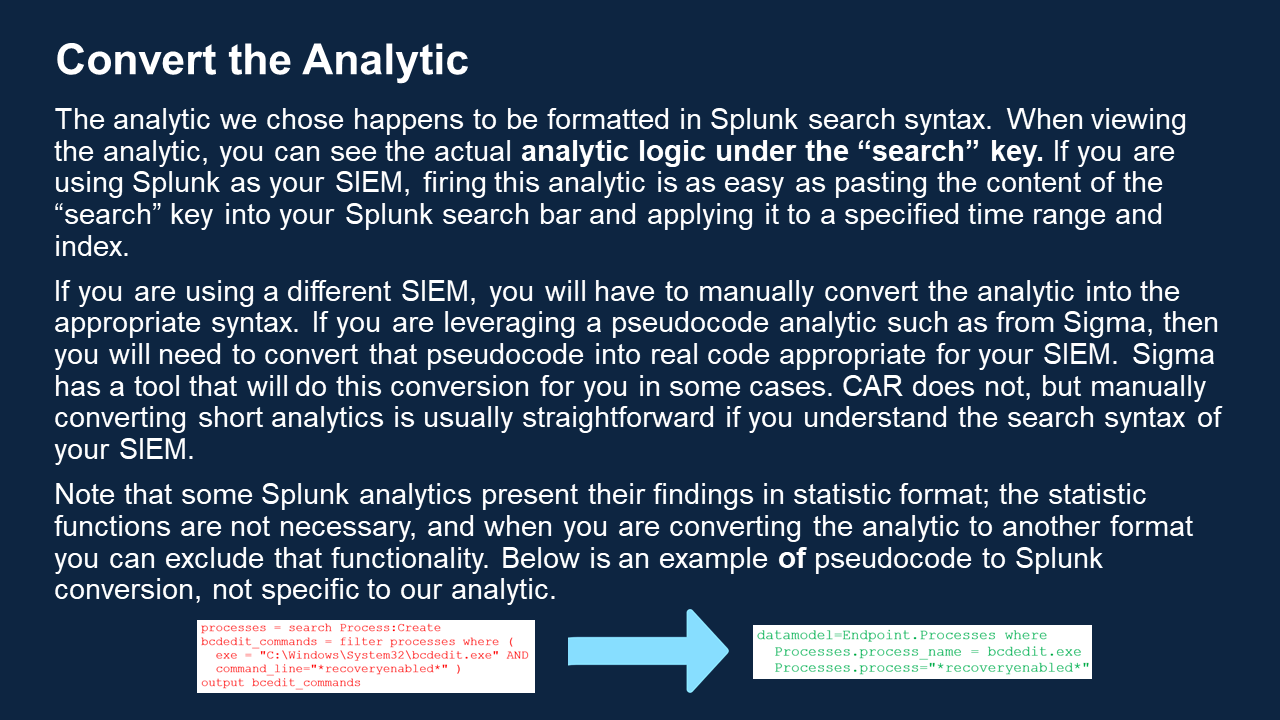
- Convert the analytic to use your data schema, if necessary.
- Test the analytic within your SIEM to see if it functions as anticipated.
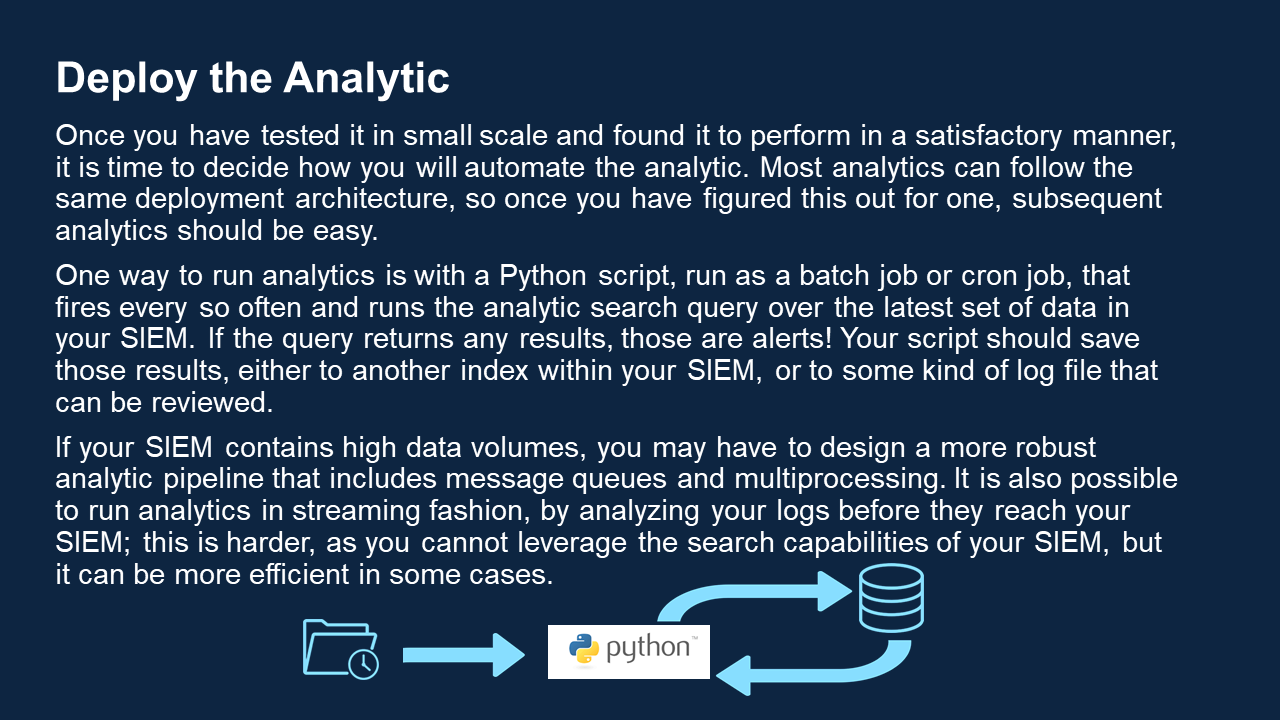
- Set up a mechanism to feed the data through your analytics. This architecture can vary. One popular method is to run batch jobs every few minutes: this method would take the latest raw data in your SIEM and apply your analytics to it, spitting any results into a new log somewhere.
- Set up a maintenance timetable that will remind you to periodically review which analytics you have deployed, and decide if they are still relevant. Some analytics can become outdated as technology and threats change
Walk through our analytic deployment scenario for an example of how this all works!
| ATTACK Technique | Name/ID | Operating System | Source Repository | Last Modified | hf:tax:attack_technique | hf:tax:operating_system | hf:tax:source_repository |
|---|---|---|---|---|---|---|---|
| T1047 |
8028c2c3-e25a-46e3-827f-bbb5abf181d7 | Windows | Sigma | November 12, 2021 | t1047 | windows | sigma |
| T1047 |
WMI Persistence – Script Event Consumer ec1d5e28-8f3b-4188-a6f8-6e8df81dc28e | Windows | Sigma | November 12, 2021 | t1047 | windows | sigma |
| T1047 |
Suspicious WMI Execution Using Rundll32 3c89a1e8-0fba-449e-8f1b-8409d6267ec8 | Windows | Sigma | November 12, 2021 | t1047 | windows | sigma |
| T1047 |
5af54681-df95-4c26-854f-2565e13cfab0 | Windows | Sigma | November 12, 2021 | t1047 | windows | sigma |
| T1047 |
T1047 Wmiprvse Wbemcomn DLL Hijack f6c68d5f-e101-4b86-8c84-7d96851fd65c | Windows | Sigma | November 12, 2021 | t1047 | windows | sigma |
| T1047 |
b7155193-8a81-4d8f-805d-88de864ca50c | Windows | Sigma | November 12, 2021 | t1047 | windows | sigma |
| T1041 |
Detect SNICat SNI Exfiltration 82d06410-134c-11eb-adc1-0242ac120002 | Windows | Splunk | November 12, 2021 | t1041 | windows | splunk |
| T1041 |
DNSCat2 Powershell Implementation Detection Via Process Creation b11d75d6-d7c1-11ea-87d0-0242ac130003 | Windows | Sigma | November 12, 2021 | t1041 | windows | sigma |
| T1041 |
Exfiltration and Tunneling Tools Execution c75309a3-59f8-4a8d-9c2c-4c927ad50555 | Windows | Sigma | November 4, 2021 | t1041 | windows | sigma |
| T1036.005 |
a51bfe1a-94f0-48cc-b4e4-16a110145893 | Windows | Splunk | November 4, 2021 | t1036-005 | windows | splunk |
| T1036.005 |
Windows Processes Suspicious Parent Directory 96036718-71cc-4027-a538-d1587e0006a7 | Windows | Sigma | November 4, 2021 | t1036-005 | windows | sigma |
| T1036.005 |
Common Windows Process Masquerading CAR-2021-04-001 | Windows | CAR | November 4, 2021 | t1036-005 | windows | car |
| T1036.005 |
File Created with System Process Name d5866ddf-ce8f-4aea-b28e-d96485a20d3d | Windows | Sigma | October 25, 2021 | t1036-005 | windows | sigma |
| T1036.005 |
Flash Player Update from Suspicious Location 4922a5dd-6743-4fc2-8e81-144374280997 | Windows | Sigma | October 25, 2021 | t1036-005 | windows | sigma |
| T1036.005 |
7993792c-5ce2-4475-a3db-a3a5539827ef | Windows | Sigma | October 25, 2021 | t1036-005 | windows | sigma |
| T1036.005 |
3f7f5b0b-5b16-476c-a85f-ab477f6dd24b | Windows | Sigma | October 25, 2021 | t1036-005 | windows | sigma |
| T1036.005 |
01d2e2a1-5f09-44f7-9fc1-24faa7479b6d | Windows | Sigma | October 25, 2021 | t1036-005 | windows | sigma |
| T1036.005 |
e22a6eb2-f8a5-44b5-8b44-a2dbd47b1144 | Windows | Sigma | October 25, 2021 | t1036-005 | windows | sigma |
| T1027 |
33339be3-148b-4e16-af56-ad16ec6c7e7b | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
e62a9f0c-ca1e-46b2-85d5-a6da77f86d1a | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
Application Whitelisting Bypass via Dnx.exe 81ebd28b-9607-4478-bf06-974ed9d53ed7 | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
b69888d4-380c-45ce-9cf9-d9ce46e67821 | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
Suspicious XOR Encoded PowerShell Command Line bb780e0c-16cf-4383-8383-1e5471db6cf9 | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
Visual Basic Command Line Compiler Usage 7b10f171-7f04-47c7-9fa2-5be43c76e535 | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
1a0d4aba-7668-4365-9ce4-6d79ab088dfd | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
cbb56d62-4060-40f7-9466-d8aaf3123f83 | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
PowerShell Base64 Encoded Shellcode 2d117e49-e626-4c7c-bd1f-c3c0147774c8 | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
RedMimicry Winnti Playbook Dropped File 130c9e58-28ac-4f83-8574-0a4cc913b97e | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
470ec5fa-7b4e-4071-b200-4c753100f49b | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
CrackMapExec PowerShell Obfuscation 6f8b3439-a203-45dc-a88b-abf57ea15ccf | Windows | Sigma | October 21, 2021 | t1027 | windows | sigma |
| T1027 |
95361ce5-c891-4b0a-87ca-e24607884a96 | Mac | Sigma | October 21, 2021 | t1027 | mac | sigma |
| T1027 |
c52a914f-3d8b-4b2a-bb75-b3991e75f8ba | Linux | Sigma | October 21, 2021 | t1027 | linux | sigma |
| T1012 |
74ad4314-482e-4c3e-b237-3f7ed3b9ca8d | Windows | Sigma | October 21, 2021 | t1012 | windows | sigma |
| T1027 |
e2072cab-8c9a-459b-b63c-40ae79e27031 | Linux | Sigma | October 21, 2021 | t1027 | linux | sigma |
| T1027 |
719c22d7-c11a-4f2c-93a6-2cfdd5412f68 | Mac | Sigma | October 21, 2021 | t1027 | mac | sigma |
| T1007 |
CAR-2016-03-001 | Linux, Mac, Windows | CAR | October 21, 2021 | t1007 | linux mac windows | car |
| T1012 |
Exports Critical Registry Keys To a File 82880171-b475-4201-b811-e9c826cd5eaa | Windows | Sigma | October 21, 2021 | t1012 | windows | sigma |
| T1012 |
Exports Registry Key To a File f0e53e89-8d22-46ea-9db5-9d4796ee2f8a | Windows | Sigma | October 21, 2021 | t1012 | windows | sigma |
| T1012 |
9a4ff3b8-6187-4fd2-8e8b-e0eae1129495 | Windows | Sigma | October 21, 2021 | t1012 | windows | sigma |
| T1012 |
SAM Registry Hive Handle Request f8748f2c-89dc-4d95-afb0-5a2dfdbad332 | Windows | Sigma | October 21, 2021 | t1012 | windows | sigma |
| T1007 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | September 10, 2021 | t1007 | linux mac windows | car |
| T1007 |
970007b7-ce32-49d0-a4a4-fbef016950bd | Windows | Sigma | September 10, 2021 | t1007 | windows | sigma |
| T1562.001 |
Defense evasion disable windows firewall rules with netsh 4b438734-3793-4fda-bd42-ceeada0be8f9 | Windows | Elastic | July 27, 2021 | t1562-001 | windows | elastic |
| T1078.002 |
CAR-2013-02-008 | Linux, Mac, Windows | CAR | July 25, 2021 | t1078-002 | linux mac windows | car |
| T1562.001 |
Defense evasion cloudwatch alarm deletion f772ec8a-e182-483c-91d2-72058f76a44c | Cloud | Elastic | July 25, 2021 | t1562-001 | cloud | elastic |
| T1053.005 |
CAR-2020-09-001 | Windows | CAR | July 19, 2021 | t1053-005 | windows | car |
| T1053.005 |
Remotely Scheduled Tasks via Schtasks CAR-2015-04-002 | Windows | CAR | July 19, 2021 | t1053-005 | windows | car |
| CAR-2021-01-008 |
CAR-2021-01-008 | Windows | CAR | July 19, 2021 | car-2021-01-008 | windows | car |
| T1548.002 |
CAR-2019-04-001 | Windows | CAR | July 19, 2021 | t1548-002 | windows | car |
| T1548.002 |
DLL Injection via Load Library CAR-2013-10-002 | Windows | CAR | July 19, 2021 | t1548-002 | windows | car |
| T1547.001 |
CAR-2020-05-003 | Windows | CAR | July 19, 2021 | t1547-001 | windows | car |
| T1547.001 |
Reg.exe called from Command Shell CAR-2013-03-001 | Windows | CAR | July 19, 2021 | t1547-001 | windows | car |
| T1547.001 |
CAR-2013-01-002 | Windows | CAR | July 19, 2021 | t1547-001 | windows | car |
| T1543.003 |
CAR-2014-05-002 | Windows | CAR | July 19, 2021 | t1543-003 | windows | car |
| T1543.003 |
Remotely Launched Executables via Services CAR-2014-03-005 | Windows | CAR | July 19, 2021 | t1543-003 | windows | car |
| T1543.003 |
CAR-2014-02-001 | Windows | CAR | July 19, 2021 | t1543-003 | windows | car |
| T1543.003 |
CAR-2013-09-005 | Windows | CAR | July 19, 2021 | t1543-003 | windows | car |
| T1543.003 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | July 19, 2021 | t1543-003 | linux mac windows | car |
| T1543.003 |
CAR-2013-01-002 | Windows | CAR | July 19, 2021 | t1543-003 | windows | car |
| T1518 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | July 19, 2021 | t1518 | linux mac windows | car |
| T1490 |
BCDEdit Failure Recovery Modification CAR-2021-05-003 | Windows | CAR | July 19, 2021 | t1490 | windows | car |
| T1490 |
Detecting Shadow Copy Deletion via Vssadmin.exe CAR-2021-01-009 | Windows | CAR | July 19, 2021 | t1490 | windows | car |
| T1490 |
CAR-2020-04-001 | Windows | CAR | July 19, 2021 | t1490 | windows | car |
| T1222.001 |
Access Permission Modification CAR-2019-07-001 | Linux, Mac, Windows | CAR | July 19, 2021 | t1222-001 | linux mac windows | car |
| T1218.011 |
CAR-2014-03-006 | Windows | CAR | July 19, 2021 | t1218-011 | windows | car |
| T1218.010 |
CAR-2019-04-003 | Windows | CAR | July 19, 2021 | t1218-010 | windows | car |
| T1218.010 |
CAR-2019-04-002 | Windows | CAR | July 19, 2021 | t1218-010 | windows | car |
| T1218.001 |
CAR-2020-11-009 | Windows | CAR | July 19, 2021 | t1218-001 | windows | car |
| T1204.002 |
CAR-2021-05-002 | Windows | CAR | July 19, 2021 | t1204-002 | windows | car |
| T1140 |
CAR-2021-05-009 | Windows | CAR | July 19, 2021 | t1140 | windows | car |
| T1134 |
Addition of SID History to Active Directory Object 2632954e-db1c-49cb-9936-67d1ef1d17d2 | Windows | Sigma | July 19, 2021 | t1134 | windows | sigma |
| T1134 |
Detection of Possible Rotten Potato 6c5808ee-85a2-4e56-8137-72e5876a5096 | Windows | Sigma | July 19, 2021 | t1134 | windows | sigma |
| T1134 |
Meterpreter or Cobalt Strike Get System Service Start 15619216-e993-4721-b590-4c520615a67d | Windows | Sigma | July 19, 2021 | t1134 | windows | sigma |
| T1134 |
Meterpreter or Cobalt Strike Get System Service Installation 843544a7-56e0-4dcc-a44f-5cc266dd97d6 | Windows | Sigma | July 19, 2021 | t1134 | windows | sigma |
| T1133 |
f88e112a-21aa-44bd-9b01-6ee2a2bbbed1 | Windows | Sigma | July 13, 2021 | t1133 | windows | sigma |
| T1112 |
Illegal Access To User Content via PowerSploit modules 01fc7d91-eb0c-478e-8633-e4fa4904463a | Windows | Splunk | July 13, 2021 | t1112 | windows | splunk |
| T1112 |
Suspicious System.Drawing Load 666ecfc7-229d-42b8-821e-1a8f8cb7057c | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
0877ed01-da46-4c49-8476-d49cdd80dfa7 | Linux | Sigma | July 13, 2021 | t1112 | linux | sigma |
| T1112 |
909f8fd8-7ac8-11eb-a1f3-acde48001122 | Windows | Splunk | July 13, 2021 | t1112 | windows | splunk |
| T1112 |
e3d3f57a-c381-11eb-9e35-acde48001122 | Windows | Splunk | July 13, 2021 | t1112 | windows | splunk |
| T1112 |
a6b3ab4e-dd77-4213-95fa-fc94701995e0 | Windows | Splunk | July 13, 2021 | t1112 | windows | splunk |
| T1112 |
Uncommon Registry Persistence Change 54902e45-3467-49a4-8abc-529f2c8cfb80 | Windows | Elastic | July 13, 2021 | t1112 | windows | elastic |
| T1112 |
4ac5fc44-a601-4c06-955b-309df8c4e9d4 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Suspicious VBoxDrvInst.exe Parameters b7b19cb6-9b32-4fc4-a108-73f19acfe262 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Non-privileged Usage of Reg or Powershell 8f02c935-effe-45b3-8fc9-ef8696a9e41d | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
DNS ServerLevelPluginDll Install e61e8a88-59a9-451c-874e-70fcc9740d67 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
d67572a0-e2ec-45d6-b8db-c100d14b8ef2 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Disable Security Events Logging Adding Reg Key MiniNt 919f2ef0-be2d-4a7a-b635-eb2b41fde044 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Sysmon Channel Reference Deletion 18beca67-ab3e-4ee3-ba7a-a46ca8d7d0cc | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Removal of Potential COM Hijacking Registry Keys 96f697b0-b499-4e5d-9908-a67bec11cdb6 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
9d3436ef-9476-4c43-acca-90ce06bdf33a | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Modifies the Registry From a File 5f60740a-f57b-4e76-82a1-15b6ff2cb134 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Imports Registry Key From a File 73bba97f-a82d-42ce-b315-9182e76c57b1 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
c3198a27-23a0-4c2c-af19-e5328d49680e | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Modifies the Registry From a ADS 77946e79-97f1-45a2-84b4-f37b5c0d8682 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
41904ebe-d56c-4904-b9ad-7a77bdf154b3 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Persistent Outlook Landing Pages ddd171b5-2cc6-4975-9e78-f0eccd08cc76 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Imports Registry Key From an ADS 0b80ade5-6997-4b1d-99a1-71701778ea61 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Remote Registry Management Using Reg Utility 68fcba0d-73a5-475e-a915-e8b4c576827e | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
b0524451-19af-4efa-a46f-562a977f792e | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Wdigest CredGuard Registry Modification 1a2d6c47-75b0-45bd-b133-2c0be75349fd | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Run Once Task Execution as Configured in Registry 198effb6-6c98-4d0c-9ea3-451fa143c45c | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
5118765f-6657-4ddb-a487-d7bd673abbf1 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Run Once Task Configuration in Registry c74d7efc-8826-45d9-b8bb-f04fac9e4eff | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Suspicious New Printer Ports in Registry (CVE-2020-1048) 7ec912f2-5175-4868-b811-ec13ad0f8567 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
d6a9b252-c666-4de6-8806-5561bbbd3bdc | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Persistent Outlook Landing Pages 487bb375-12ef-41f6-baae-c6a1572b4dd1 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
RDP Sensitive Settings Changed 171b67e1-74b4-460e-8d55-b331f3e32d67 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Registry Entries For Azorult Malware f7f9ab88-7557-4a69-b30e-0a8f91b3a0e7 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
21f17060-b282-4249-ade0-589ea3591558 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
Office Security Settings Changed a166f74e-bf44-409d-b9ba-ea4b2dd8b3cd
| Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
RedMimicry Winnti Playbook Registry Manipulation 5b175490-b652-4b02-b1de-5b5b4083c5f8 | Windows | Sigma | July 13, 2021 | t1112 | windows | sigma |
| T1112 |
CAR-2014-11-005 | Windows | CAR | July 13, 2021 | t1112 | windows | car |
| T1112 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | July 13, 2021 | t1112 | linux mac windows | car |
| T1112 |
CAR-2013-01-002 | Windows | CAR | July 13, 2021 | t1112 | windows | car |
| T1110.001 |
High Number of Login Failures from a single source 7f398cfb-918d-41f4-8db8-2e2474e02222 | Experimental | Splunk | July 13, 2021 | t1110-001 | experimental | splunk |
| T1107 |
39a80702-d7ca-4a83-b776-525b1f86a36d | Windows | Sigma | July 13, 2021 | t1107 | windows | sigma |
| T1107 |
71d65515-c436-43c0-841b-236b1f32c21e | Network | Sigma | July 13, 2021 | t1107 | network | sigma |
| T1107 |
9703792d-fd9a-456d-a672-ff92efe4806a | Windows | Sigma | July 13, 2021 | t1107 | windows | sigma |
| T1106 |
Illegal Service and Process Control via PowerSploit modules 0e910e5b-309d-4bc3-8af2-0030c02aa353 | Windows | Splunk | July 13, 2021 | t1106 | windows | splunk |
| T1106 |
Illegal Service and Process Control via Mimikatz modules aaf3adf1-73e1-4477-b4ee-3771898964f1 | Windows | Splunk | July 13, 2021 | t1106 | windows | splunk |
| T1106 |
Suspicious SolarWinds Child Process 93b22c0a-06a0-4131-b830-b10d5e166ff4 | Windows | Elastic | July 13, 2021 | t1106 | windows | elastic |
| T1106 |
Accessing WinAPI in PowerShell 03d83090-8cba-44a0-b02f-0b756a050306 | Windows | Sigma | July 13, 2021 | t1106 | windows | sigma |
| T1106 |
Possible App Whitelisting Bypass via WinDbg/CDB as a Shellcode Runner b5c7395f-e501-4a08-94d4-57fe7a9da9d2 | Windows | Sigma | July 13, 2021 | t1106 | windows | sigma |
| T1106 |
RedMimicry Winnti Playbook Execute 95022b85-ff2a-49fa-939a-d7b8f56eeb9b | Windows | Sigma | July 13, 2021 | t1106 | windows | sigma |
| T1105 |
58194e28-ae5e-11eb-8912-acde48001122 | Windows | Splunk | July 13, 2021 | t1105 | windows | splunk |
| T1105 |
Suspicious Curl Network Connection 3f613dc0-21f2-4063-93b1-5d3c15eef22f | Experimental | Splunk | July 13, 2021 | t1105 | experimental | splunk |
| T1105 |
Office Product Spawning CertUtil 6925fe72-a6d5-11eb-9e17-acde48001122 | Windows | Splunk | July 13, 2021 | t1105 | windows | splunk |
| T1105 |
80630ff4-8e4c-11eb-aab5-acde48001122 | Windows | Splunk | July 13, 2021 | t1105 | windows | splunk |
| T1105 |
CertUtil Download With VerifyCtl and Split Arguments 801ad9e4-8bfb-11eb-8b31-acde48001122 | Windows | Splunk | July 13, 2021 | t1105 | windows | splunk |
| T1105 |
CertUtil Download With URLCache and Split Arguments 415b4306-8bfb-11eb-85c4-acde48001122 | Windows | Splunk | July 12, 2021 | t1105 | windows | splunk |
| T1105 |
Command And Control Download RAR Powershell from Internet ff013cb4-274d-434a-96bb-fe15ddd3ae92 | Network | Elastic | July 12, 2021 | t1105 | network | elastic |
| T1105 |
Apple Script Execution followed by Network Connection 47f76567-d58a-4fed-b32b-21f571e28910 | Mac | Elastic | July 12, 2021 | t1105 | mac | elastic |
| T1105 |
Execution command prompt connecting to the internet 89f9a4b0-9f8f-4ee0-8823-c4751a6d6696 | Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1105 |
Remote File Download via PowerShell 33f306e8-417c-411b-965c-c2812d6d3f4d | Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1105 |
Remote File Download via MpCmdRun c6453e73-90eb-4fe7-a98c-cde7bbfc504a
| Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1078.003 |
Detect Excessive User Account Lockouts 95a7f9a5-6096-437e-a19e-86f42ac609bd | Mac | Elastic | July 12, 2021 | t1078-003 | mac | elastic |
| T1091 |
External Disk Drive or USB Storage Device f69a87ea-955e-4fb4-adb2-bb9fd6685632 | Windows | Sigma | July 12, 2021 | t1091 | windows | sigma |
| T1095 |
f7158a64-6204-4d6d-868a-6e6378b467e0 | Linux | Sigma | July 12, 2021 | t1095 | linux | sigma |
| T1095 |
Detect Large Outbound ICMP Packets e9c102de-4d43-42a7-b1c8-8062ea297419 | Experimental | Splunk | July 12, 2021 | t1095 | experimental | splunk |
| T1105 |
CAR-2013-07-001 | Linux, Mac, Windows | CAR | July 12, 2021 | t1105 | linux mac windows | car |
| T1105 |
CAR-2021-05-005 | Windows | CAR | July 12, 2021 | t1105 | windows | car |
| T1105 |
CertUtil Download With URLCache and Split Arguments CAR-2021-05-006 | Windows | CAR | July 12, 2021 | t1105 | windows | car |
| T1105 |
CertUtil Download With VerifyCtl and Split Arguments CAR-2021-05-007 | Windows | CAR | July 12, 2021 | t1105 | windows | car |
| T1105 |
7a14080d-a048-4de8-ae58-604ce58a795b | Linux | Sigma | July 12, 2021 | t1105 | linux | sigma |
| T1105 |
d7825193-b70a-48a4-b992-8b5b3015cc11 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Microsoft Binary Suspicious Communication Endpoint e0f8ab85-0ac9-423b-a73a-81b3c7b1aa97 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
f7b5f842-a6af-4da5-9e95-e32478f3cd2f | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
5e51acb2-bcbe-435b-99c6-0e3cd5e2aa59 | Network | Sigma | July 12, 2021 | t1105 | network | sigma |
| T1105 |
47e0852a-cf81-4494-a8e6-31864f8c86ed | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
21dd6d38-2b18-4453-9404-a0fe4a0cc288 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Finger.exe Suspicious Invocation af491bca-e752-4b44-9c86-df5680533dbc | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Malicious Payload Download via Office Binaries 0c79148b-118e-472b-bdb7-9b57b444cc19 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Windows Defender Download Activity 46123129-1024-423e-9fae-43af4a0fa9a5 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Suspicious Curl Usage on Windows e218595b-bbe7-4ee5-8a96-f32a24ad3468 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
8f70ac5f-1f6f-4f8e-b454-db19561216c5 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
aac2fd97-bcba-491b-ad66-a6edf89c71bf | Network | Sigma | July 12, 2021 | t1105 | network | sigma |
| T1105 |
GfxDownloadWrapper.exe Downloads File from Suspicious URL eee00933-a761-4cd0-be70-c42fe91731e7 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Microsoft Binary Github Communication 635dbb88-67b3-4b41-9ea5-a3af2dd88153 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Suspicious Desktop Image Downloader Target File fc4f4817-0c53-4683-a4ee-b17a64bc1039 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Command Line Execution with Suspicious URL and AppData Strings 1ac8666b-046f-4201-8aba-1951aaec03a3 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
855bc8b5-2ae8-402e-a9ed-b889e6df1900 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
e011a729-98a6-4139-b5c4-bf6f6dd8239a | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
3711eee4-a808-4849-8a14-faf733da3612 | Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1105 |
Download from Suspicious Dyndns Hosts 195c1119-ef07-4909-bb12-e66f5e07bf3c | Proxy | Sigma | July 12, 2021 | t1105 | proxy | sigma |
| T1105 |
Remote File Copy via TeamViewer b25a7df2-120a-4db2-bd3f-3e4b86b24bee | Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1105 |
Remote File Download via Script Interpreter 1d276579-3380-4095-ad38-e596a01bc64f | Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1105 |
Remote File Download via Desktop Image Downloader Utility 15c0b7a7-9c34-4869-b25b-fa6518414899 | Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1105 |
Network Connection via Certutil 3838e0e3-1850-4850-a411-2e8c5ba40ba8 | Windows | Elastic | July 12, 2021 | t1105 | windows | elastic |
| T1105 |
Suspicious Desktop Image Downloader Command bb58aa4a-b80b-415a-a2c0-2f65a4c81009
| Windows | Sigma | July 12, 2021 | t1105 | windows | sigma |
| T1078.003 |
Privilege escalation local user added to admin 565c2b44-7a21-4818-955f-8d4737967d2e | Mac | Elastic | July 11, 2021 | t1078-003 | mac | elastic |
| T1078.003 |
Persistence account creation hide at logon 41b638a1-8ab6-4f8e-86d9-466317ef2db5 | Mac | Elastic | July 11, 2021 | t1078-003 | mac | elastic |
| T1078.003 |
Persistence enable root account cc2fd2d0-ba3a-4939-b87f-2901764ed036 | Mac | Elastic | July 11, 2021 | t1078-003 | mac | elastic |
| T1078.003 |
0f63e1ef-1eb9-4226-9d54-8927ca08520a | Windows | Sigma | July 11, 2021 | t1078-003 | windows | sigma |
| T1078.003 |
User Login Activity Monitoring CAR-2013-10-001 | Linux, Mac, Windows | CAR | July 11, 2021 | t1078-003 | linux mac windows | car |
| T1078.003 |
CAR-2013-05-005 | Linux, Mac, Windows | CAR | July 11, 2021 | t1078-003 | linux mac windows | car |
| T1078.003 |
CAR-2013-05-003 | Linux, Mac, Windows | CAR | July 11, 2021 | t1078-003 | linux mac windows | car |
| T1078.003 |
User Logged in to Multiple Hosts CAR-2013-02-012 | Linux, Mac, Windows | CAR | July 11, 2021 | t1078-003 | linux mac windows | car |
| T1053.005 |
Suspicious Scheduled Task from Public Directory 7feb7972-7ac3-11eb-bac8-acde48001122 | Windows | Splunk | July 11, 2021 | t1053-005 | windows | splunk |
| T1059.001 |
Invoke-Obfuscation STDIN+ Launcher 6c96fc76-0eb1-11eb-adc1-0242ac120002 | Windows | Sigma | July 11, 2021 | t1059-001 | windows | sigma |
| T1053.005 |
CAR-2013-08-001 | Windows | CAR | July 11, 2021 | t1053-005 | windows | car |
| T1059.001 |
Invoke-Obfuscation Via Use Clip e1561947-b4e3-4a74-9bdd-83baed21bdb5 | Windows | Sigma | July 11, 2021 | t1059-001 | windows | sigma |
| T1562.001 |
Impact cloud watch log stream deletion d624f0ae-3dd1-4856-9aad-ccfe4d4bfa17 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion waf acl deletion 91d04cd4-47a9-4334-ab14-084abe274d49 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion event hub deletion e0f36de1-0342-453d-95a9-a068b257b053 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Impact cloud watch log group deletion 68a7a5a5-a2fc-4a76-ba9f-26849de881b4 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion SolarWinds backdoor service disabled via registry b9960fef-82c6-4816-befa-44745030e917 | Windows | Elastic | July 11, 2021 | t1562-001 | windows | elastic |
| T1562.001 |
Defense evasion network watcher deletion 323cb487-279d-4218-bcbd-a568efe930c6 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion guard duty detector deletion 523116c0-d89d-4d7c-82c2-39e6845a78ef | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion cloudtrail logging suspended 1aa8fa52-44a7-4dae-b058-f3333b91c8d7 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion firewall policy deletion e02bd3ea-72c6-4181-ac2b-0f83d17ad969 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion ec2 flow log deletion 9395fd2c-9947-4472-86ef-4aceb2f7e872 | Cloud | Elastic | July 11, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion apple software updates modification f683dcdf-a018-4801-b066-193d4ae6c8e5 | Mac | Elastic | July 11, 2021 | t1562-001 | mac | elastic |
| T1562.001 |
Defense evasion attempt to disable syslog service 2f8a1226-5720-437d-9c20-e0029deb6194 | Linux | Elastic | July 11, 2021 | t1562-001 | linux | elastic |
| T1562.001 |
Defense evasion scheduled jobs at protocol enabled 9aa0e1f6-52ce-42e1-abb3-09657cee2698 | Windows | Elastic | July 11, 2021 | t1562-001 | windows | elastic |
| T1562.001 |
Defense evasion waf rule or rule group deletion 5beaebc1-cc13-4bfc-9949-776f9e0dc318 | Cloud | Elastic | July 8, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion cloudtrail logging deleted 7024e2a0-315d-4334-bb1a-441c593e16ab | Cloud | Elastic | July 8, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion azure diagnostic settings deletion 5370d4cd-2bb3-4d71-abf5-1e1d0ff5a2de | Cloud | Elastic | July 8, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion attempt del quarantine attrib f0b48bbc-549e-4bcf-8ee0-a7a72586c6a7 | Mac | Elastic | July 8, 2021 | t1562-001 | mac | elastic |
| T1562.001 |
Defense evasion configuration recorder stopped fbd44836-0d69-4004-a0b4-03c20370c435 | Cloud | Elastic | July 8, 2021 | t1562-001 | cloud | elastic |
| T1562.001 |
Defense evasion defender disabled via registry 2ffa1f1e-b6db-47fa-994b-1512743847eb | Windows | Elastic | July 8, 2021 | t1562-001 | windows | elastic |
| T1562.001 |
Defense evasion safari config change 6482255d-f468-45ea-a5b3-d3a7de1331ae | Mac | Elastic | July 8, 2021 | t1562-001 | mac | elastic |
| T1562.001 |
Defense evasion privacy controls tcc database modification eea82229-b002-470e-a9e1-00be38b14d32 | Mac | Elastic | July 8, 2021 | t1562-001 | mac | elastic |
| T1562.001 |
Defense evasion amenable key mod f874315d-5188-4b4a-8521-d1c73093a7e4 | Windows | Elastic | July 8, 2021 | t1562-001 | windows | elastic |
| T1562.001 |
Defense evasion port forwarding added registry 3535c8bb-3bd5-40f4-ae32-b7cd589d5372 | Windows | Elastic | July 7, 2021 | t1562-001 | windows | elastic |
| T1562.001 |
Defense evasion disable selinux attempt eb9eb8ba-a983-41d9-9c93-a1c05112ca5e
| Linux | Elastic | July 7, 2021 | t1562-001 | linux | elastic |
| T1562.001 |
Defense evasion unload endpointsecurity text 70fa1af4-27fd-4f26-bd03-50b6af6b9e24 | Mac | Elastic | July 7, 2021 | t1562-001 | mac | elastic |
| T1562.001 |
Detecting Tampering of Windows Defender Command Prompt CAR-2021-01-007 | Windows | CAR | July 7, 2021 | t1562-001 | windows | car |
| T1562.001 |
User Activity from Stopping Windows Defensive Services CAR-2016-04-003 | Windows | CAR | July 7, 2021 | t1562-001 | windows | car |
| T1562.001 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | July 7, 2021 | t1562-001 | linux mac windows | car |
| T1553.002 |
56557cde-d923-4b88-adee-c61b3f3b5dc3 | Windows | Elastic | July 7, 2021 | t1553-002 | windows | elastic |
| T1053.005 |
Schtasks used for forcing a reboot 1297fb80-f42a-4b4a-9c8a-88c066437cf6 | Windows | Splunk | July 7, 2021 | t1053-005 | windows | splunk |
| T1053.005 |
Scheduled Task Deleted Or Created via CMD d5af132c-7c17-439c-9d31-13d55340f36c | Windows | Splunk | July 7, 2021 | t1053-005 | windows | splunk |
| T1053.005 |
Schtasks scheduling job on remote system 1297fb80-f42a-4b4a-9c8a-88c066237cf6 | Windows | Splunk | July 7, 2021 | t1053-005 | windows | splunk |
| T1053.005 |
WinEvent Scheduled Task Created to Spawn Shell 203ef0ea-9bd8-11eb-8201-acde48001122 | Windows | Splunk | July 7, 2021 | t1053-005 | windows | splunk |
| T1053.005 |
WinEvent Scheduled Task Created Within Public Path 5d9c6eee-988c-11eb-8253-acde48001122 | Windows | Splunk | July 7, 2021 | t1053-005 | windows | splunk |
| T1053.005 |
Schedule Task with HTTP Command Arguments 523c2684-a101-11eb-916b-acde48001122 | Windows | Splunk | July 7, 2021 | t1053-005 | windows | splunk |
| T1059.001 |
CAR-2014-04-003 | Windows | CAR | July 7, 2021 | t1059-001 | windows | car |
| T1059.001 |
CAR-2014-11-004 | Windows | CAR | July 7, 2021 | t1059-001 | windows | car |
| T1059.001 |
ac7102b4-9e1e-4802-9b4f-17c5524c015c | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation VAR++ LAUNCHER OBFUSCATION e9f55347-2928-4c06-88e5-1a7f8169942e | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
fdb62a13-9a81-4e5c-a38f-ea93a16f6d7c | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
e32d4572-9826-4738-b651-95fa63747e8a | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
PowerShell Encoded Character Syntax e312efd0-35a1-407f-8439-b8d434b438a6 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
88f680b8-070e-402c-ae11-d2914f2257f1 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
a6d67db4-6220-436d-8afc-f3842fe05d43 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
9c14c9fa-1a63-4a64-8e57-d19280559490
| Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation VAR+ Launcher 27aec9c9-dbb0-4939-8422-1742242471d0 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Suspicious PowerShell Invocations – Generic 3d304fda-78aa-43ed-975c-d740798a49c1 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation CLIP+ Launcher b222df08-0e07-11eb-adc1-0242ac120002 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation Via Use MSHTA ac20ae82-8758-4f38-958e-b44a3140ca88 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1562.001 |
Defense evasion attempt to disable iptables or firewall 125417b8-d3df-479f-8418-12d7e034fee3 | Linux | Elastic | July 7, 2021 | t1562-001 | linux | elastic |
| T1562.001 |
Defense evasion enable inbound rdp with netsh 074464f9-f30d-4029-8c03-0ed237fffec7 | Windows | Elastic | July 7, 2021 | t1562-001 | windows | elastic |
| T1059.001 |
Invoke-Obfuscation RUNDLL LAUNCHER 056a7ee1-4853-4e67-86a0-3fd9ceed7555 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1562.001 |
Defense evasion stop process service threshold 035889c4-2686-4583-a7df-67f89c292f2c | Windows | Elastic | July 7, 2021 | t1562-001 | windows | elastic |
| T1059.001 |
Invoke-Obfuscation Via Use Rundll32 36c5146c-d127-4f85-8e21-01bf62355d5a | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1552.001 |
Credentials in Files & Registry CAR-2020-09-004 | Windows | CAR | July 7, 2021 | t1552-001 | windows | car |
| T1552.001 |
Credential access collection sensitive files 6b84d470-9036-4cc0-a27c-6d90bbfe81ab | Linux | Elastic | July 7, 2021 | t1552-001 | linux | elastic |
| T1552.001 |
Credential access key vault modified 792dd7a6-7e00-4a0a-8a9a-a7c24720b5ec | Cloud | Elastic | July 7, 2021 | t1552-001 | cloud | elastic |
| T1059.001 |
Suspicious XOR Encoded PowerShell Command Line 812837bb-b17f-45e9-8bd0-0ec35d2e3bd6 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Too Long PowerShell Commandlines d0d28567-4b9a-45e2-8bbc-fb1b66a1f7f6 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Suspicious CLR Logs Creation e4b63079-6198-405c-abd7-3fe8b0ce3263 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
PowerShell Called from an Executable Version Mismatch c70e019b-1479-4b65-b0cc-cd0c6093a599 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Suspicious PowerShell Download 65531a81-a694-4e31-ae04-f8ba5bc33759 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation COMPRESS OBFUSCATION 7eedcc9d-9fdb-4d94-9c54-474e8affc0c7 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
867613fb-fa60-4497-a017-a82df74a172c | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Accessing WinAPI in PowerShell. Code Injection. eeb2e3dc-c1f4-40dd-9bd5-149ee465ad50 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
86b896ba-ffa1-4fea-83e3-ee28a4c915c7 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation Via Use Clip db92dd33-a3ad-49cf-8c2c-608c3e30ace0 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
3b6ab547-8ec2-4991-b9d2-2b06702a48d7 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
Invoke-Obfuscation VAR++ LAUNCHER OBFUSCATION e54f5149-6ba3-49cf-b153-070d24679126 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
fe6e002f-f244-4278-9263-20e4b593827f | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
243de76f-4725-4f2e-8225-a8a69b15ad61 | Windows | Sigma | July 7, 2021 | t1059-001 | windows | sigma |
| T1059.001 |
1a93b7ea-7af7-11eb-adb5-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
4d015ef2-7adf-11eb-95da-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Detect SharpHound Command-Line Arguments a0bdd2f6-c2ff-11eb-b918-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
dd04b29a-beed-11eb-87bc-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Detect SharpHound File Modifications 42b4b438-beed-11eb-ba1d-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Malicious PowerShell Process With Obfuscation Techniques cde75cf6-3c7a-4dd6-af01-27cdb4511fd4 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Set Default PowerShell Execution Policy To Unrestricted or Bypass c2590137-0b08-4985-9ec5-6ae23d92f63d | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Malicious PowerShell Process – Execution Policy Bypass 9be56c82-b1cc-4318-87eb-d138afaaca39 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Malicious PowerShell Process – Connect To Internet With Hidden Window ee18ed37-0802-4268-9435-b3b91aaa18db | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
1a382c6c-7c2e-11eb-ac69-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Powershell Processing Stream Of Data 0d718b52-c9f1-11eb-bc61-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Detect AzureHound Command-Line Arguments 26f02e96-c300-11eb-b611-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Detect AzureHound File Modifications 1c34549e-c31b-11eb-996b-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.001 |
Detect Mimikatz Using Loaded Images 29e307ba-40af-4ab2-91b2-3c6b392bbba0 | Windows | Splunk | July 7, 2021 | t1059-001 | windows | splunk |
| T1059.003 |
CAR-2013-02-003 | Windows | CAR | July 7, 2021 | t1059-003 | windows | car |
| T1059.003 |
CAR-2014-11-002 | Windows | CAR | July 7, 2021 | t1059-003 | windows | car |
| T1059.003 |
Cmd.exe CommandLine Path Traversal 087790e3-3287-436c-bccf-cbd0184a7db1 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
f0b70adb-0075-43b0-9745-e82a1c608fcc | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
e507feb7-5f73-4ef6-a970-91bb6f6d744f | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
ba778144-5e3d-40cf-8af9-e28fb1df1e20 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
2b30fa36-3a18-402f-a22d-bf4ce2189f35 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
5cddf373-ef00-4112-ad72-960ac29bac34 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
Command Line Execution with Suspicious URL and AppData Strings 1ac8666b-046f-4201-8aba-1951aaec03a3 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
AWS EC2 Startup Shell Script Change 1ab3c5ed-5baf-417b-bb6b-78ca33f6c3df | Cloud | Sigma | July 7, 2021 | t1059-003 | cloud | sigma |
| T1059.003 |
52cad028-0ff0-4854-8f67-d25dfcbc78b4 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
023394c4-29d5-46ab-92b8-6a534c6f447b | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
Exploiting SetupComplete.cmd CVE-2019-1378 1c373b6d-76ce-4553-997d-8c1da9a6b5f5 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
Exploited CVE-2020-10189 Zoho ManageEngine 846b866e-2a57-46ee-8e16-85fa92759be7 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1078.002 |
Detect Excessive User Account Lockouts 95a7f9a5-6096-437e-a19e-86f42ac609bd | Windows | Splunk | July 7, 2021 | t1078-002 | windows | splunk |
| T1059.003 |
CrackMapExec Command Execution 058f4380-962d-40a5-afce-50207d36d7e2 | Windows | Sigma | July 7, 2021 | t1059-003 | windows | sigma |
| T1059.003 |
Detect Prohibited Applications Spawning cmd exe dcfd6b40-42f9-469d-a433-2e53f7486664 | Windows | Splunk | July 7, 2021 | t1059-003 | windows | splunk |
| T1059.003 |
Detect Use of cmd exe to Launch Script Interpreters b89919ed-fe5f-492c-b139-95dbb162039e | Windows | Splunk | July 7, 2021 | t1059-003 | windows | splunk |
| T1059.003 |
538d0152-7aaa-11eb-beaa-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-003 | windows | splunk |
| T1059.003 |
eb277ba0-b96b-11eb-b00e-acde48001122 | Windows | Splunk | July 7, 2021 | t1059-003 | windows | splunk |
| T1059.005 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | July 7, 2021 | t1059-005 | linux mac windows | car |
| T1059.005 |
WSF/JSE/JS/VBA/VBE File Execution 1e33157c-53b1-41ad-bbcc-780b80b58288 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
966e4016-627f-44f7-8341-f394905c361f | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
Application Whitelisting Bypass via Bginfo aaf46cdc-934e-4284-b329-34aa701e3771 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
b730a276-6b63-41b8-bcf8-55930c8fc6ee | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
8d63dadf-b91b-4187-87b6-34a1114577ea | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
Powershell Reverse Shell Connection edc2f8ae-2412-4dfd-b9d5-0c57727e70be | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
CACTUSTORCH Remote Thread Creation 2e4e488a-6164-4811-9ea1-f960c7359c40 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1053.005 |
CAR-2013-01-002 | Windows | CAR | July 7, 2021 | t1053-005 | windows | car |
| T1053.005 |
Quick execution of a series of suspicious commands CAR-2013-04-002 | Linux, Mac, Windows | CAR | July 7, 2021 | t1053-005 | linux mac windows | car |
| T1059.005 |
4fcac6eb-0287-4090-8eea-2602e4c20040 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
cea72823-df4d-4567-950c-0b579eaf0846 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
Exchange PowerShell Snap-Ins Used by HAFNIUM 25676e10-2121-446e-80a4-71ff8506af47 | Web | Sigma | July 7, 2021 | t1059-005 | web | sigma |
| T1059.005 |
Suspicious Scripting in a WMI Consumer fe21810c-2a8c-478f-8dd3-5a287fb2a0e0 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
5cddf373-ef00-4112-ad72-960ac29bac34 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
52cad028-0ff0-4854-8f67-d25dfcbc78b4 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
Windows Shell Spawning Suspicious Program 3a6586ad-127a-4d3b-a677-1e6eacdf8fde | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
1fac1481-2dbc-48b2-9096-753c49b4ec71 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1059.005 |
Suspicious File Characteristics Due to Missing Fields 9637e8a5-7131-4f7f-bdc7-2b05d8670c43 | Windows | Sigma | July 7, 2021 | t1059-005 | windows | sigma |
| T1078.002 |
User Login Activity Monitoring CAR-2013-10-001 | Linux, Mac, Windows | CAR | July 6, 2021 | t1078-002 | linux mac windows | car |
| T1078.002 |
Detect Excessive Account Lockouts From Endpoint c026e3dd-7e18-4abb-8f41-929e836efe74 | Windows | Splunk | July 6, 2021 | t1078-002 | windows | splunk |
| T1059.005 |
401e5d00-b944-11ea-8f9a-00163ecd60ae | Windows | Sigma | July 6, 2021 | t1059-005 | windows | sigma |
| T1078.002 |
CAR-2013-05-003 | Linux, Mac, Windows | CAR | July 6, 2021 | t1078-002 | linux mac windows | car |